
Magniber (MyDecryptor) Ransomware
March 13, 2023
Magniber ransomware is a very tricky example of the ransomware family. This gang is possibly one of the most peculiar ones - for both payload and activity. First activity of this ransomware group was noted in late 2017, primarily in South Korea. With time, this group became more and more creative. Uniqueness is always the stimulus for long-living, at least on the ransomware market.
At a glance, it is not so clear why that ransomware is so unique. It shares a lot of similarities with other ransomware examples. For example, it uses AES-128 encryption in CBC mode for most strains; supposedly, some of the variants apply RSA-2048 cipher. Same encryption mechanism is chosen by most of the ransomware families - it is reliable enough and does not cause a lot of CPU load during the encryption process. Same as most of the ransomware, it leaves the ransom note as a plain text file and duplicates it with a .pdf file that is opened in the web browser window. But the bigger scale you choose - the more interesting details you spot.
First thing that comes into sight - when you are trying to find the information about this ransomware - is the payment method. While most of the ransomware variants that aim at individuals rely on victim IDs, this one gives the victim a link to a landing page in the Darknet. That is more usual for gangs that attack small companies rather than ordinary users.
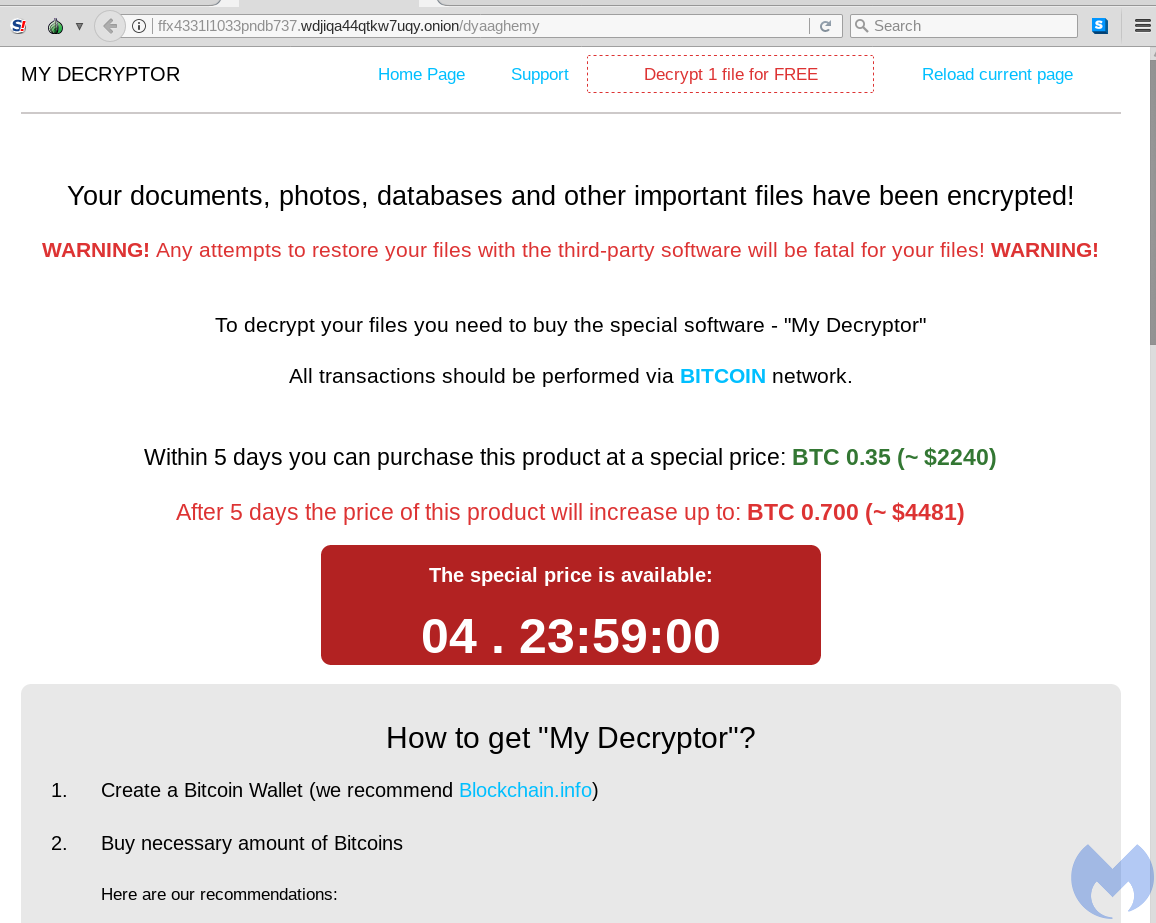
Magniber ransomware distribution
Since the appearance in 2017, this ransomware group has changed their spreading method several times. However, the overall vector of attack remained the same. Magniber ransomware uses exploits in various application software to infiltrate into the users’ systems. That makes the injection process much less dependent on the user’s actions. Once again - ransomware that aims at individual users applies exploits as the distribution way. We cannot name even a single other family that acts the same. Most of the ones are getting into the victims’ PCs through infected MS Office files or trojan-downloaders (droppers), and exploits are more usual for the ransomware that aim at corporations.
At the beginning of its history, Magniber developers were using the Magnitude exploit kit. That EK is much older than this ransomware - first use of it happened in 2013. Cybersecurity community know Magnitude for Cerber ransomware distribution. However, it was also involved in several other, less famous spreading campaigns. Being oriented on Asia Pacific (APAC) users, this EK was an obvious choice for cybercriminals who were going to attack South Korea. In particular, to spread Magniber ransomware cybercriminals used a CVE-2016-0189 - vulnerability in the JScript/VBScript engines in the Internet Explorer.
Print Spooler exploit usage
The exact choice of the exploits to use in the attack depends on the moment when its distributors decide to start the activity. In particular, in 2021 this group was active in July. For the attacks committed at that point of time the attack vector was built around a so-called PrintNightmare exploit. That vulnerability (CVE-2021-34527) allows the remote code execution in just a few steps, and relies on the breaches in Windows Print Spooler. However, this exact exploit is not a single thing that the ransomware group used. As investigations show, in a certain number of attacks crooks also used some complementary security breaches that touch other elements of the printing devices management in Windows. In particular, there was CVE-2021-34481 - that touches the Print Spooler, too. The exact mechanism of exploitation was pretty usual - they were launching a script that exploits the aforementioned breaches, downloading the malware and executing it with highest privileges.
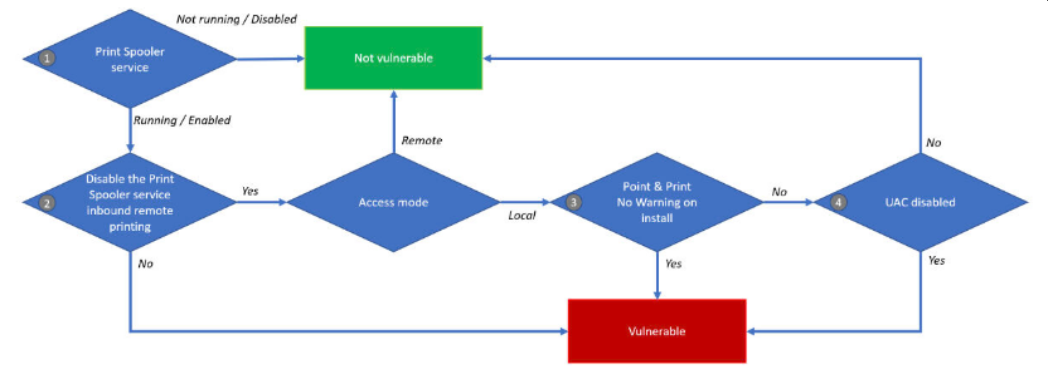
Slipping through no-zero-trust policy
The next episode of Magniber ransomware activity happened in February-March 2022. This time, fraudsters aimed at vulnerabilities in web browsers based on Chromium core. In particular, they used the fake “Update your browser” message to trick the users to install the payload. The overwhelming majority of victims say about seeing these fake pages in Chrome and Edge browsers. The vulnerability used in these attacks is rather a design flaw than a real exploit. Both antivirus tools and the internal security layers in web browsers apply the rule “if it is related to a legit app (browser for that case) and is launched by the user - it is benevolent and must not be checked”. To prevent even the minimal doubts, fraudsters also provided that file with a counterfeited certificate, signed by Microsoft. That rule, exactly, makes the attack possible. Users download the .appx file with a pseudo-update and run it, circumventing the security gates. Only security tools with zero-trust policy can catch such tricky malware.
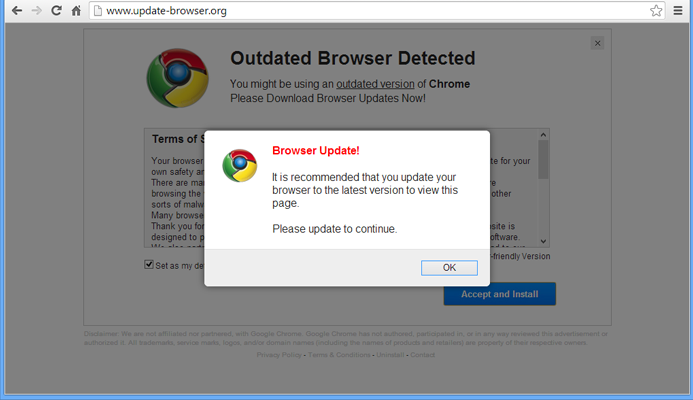
Encryption trivia
After the successful injection, this malware begins the action. Primarily to the encryption it establishes all required connections and escalates the privileges with the use of aforementioned exploits. Then, it unpacks the code that is stored in the data section of its .exe file, and injects it into each process that does not belong to the operating system. For better reliability, it duplicates the main payload with the code which is stored in the rest of the executable file sections. Acting as a virus is something new for ransomware, and in particular - ransomware that attacks individuals.
The exact ciphering process is divided into two parts, depending on the files that are encrypted during it. First, when malware works with files of almost 720 different formats (extensions), including .docx and .jpeg, it runs with a high priority. Then, when the turn of the other 32 formats comes - .swf and .zip, for example, it runs with a low priority. Such a division is likely needed to cipher the files that are the easiest for encryption as fast as possible, and then take care of the rest. SWF, ZIP and similar files are harder to cipher because of the bigger file size.
As it was mentioned, Magniber ransomware uses the AES-128 and RSA-2048 keys. Some variants combine both of these techniques, creating an even stronger cipher. It is still not the strongest key - the elliptical cipher used by LockBit ransomware is even more unbreakable - but strong enough to prevent the decryption or key interception in any way.
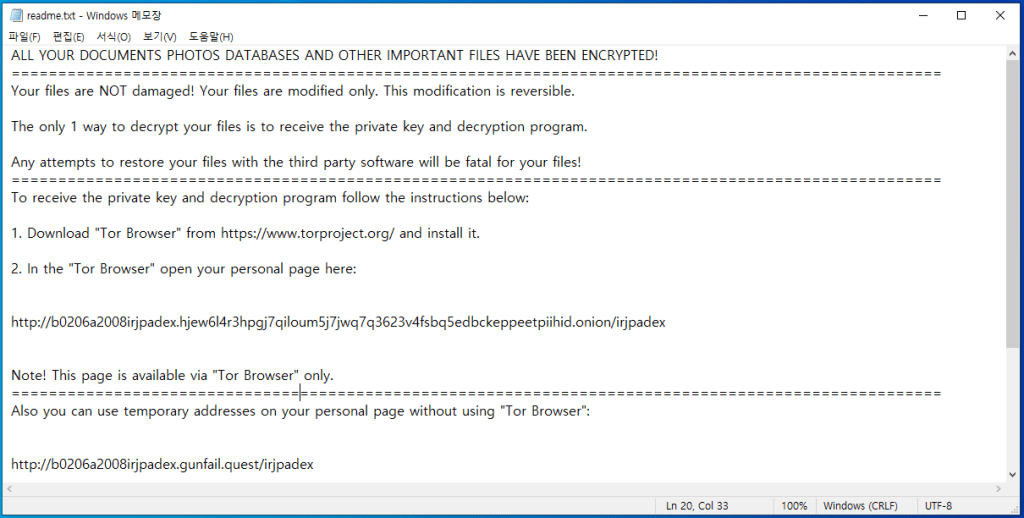
Another element that is not usual for ransomware, but looks pretty obvious, is applying a unique extension for each small group or even each individual case of injection. Up to 10-symbol extensions, that consist generally of random letters, are rarely repeated. Therefore, it will be pretty hard for individuals to find the specific advice online - no one will likely publish the information about it. And vice versa - sites will likely ignore that theme, because writing an article for each extension (there are 196 of them as of 05/03/2022) is a useless job. Publishing a comprehensive article is a possible solution, but for some reasons only a few did it.
Is Magniber decryptable?
Some of the online newsletters publish the information that Magniber ransomware encryption can be decrypted. They’re wrong, but such rumours could not appear from nowhere. South Korean cybersecurity analysts, being amidst the Magniber outbreak in 2017-2018, collected the keys for 14 variants of this ransomware. That helped the victims to get their files back, even though there were a few of them. However, the spontaneity of the activity of this ransomware makes it much harder to organise any centralised actions against this ransomware.
If you got this nasty ransomware on your computer, don’t worry. Try to use file recovery tools, backups or external drives that contain the copies of the encrypted files. One thing you must know for sure - it is obligatory to remove the ransomware first. With malware running in the background, you will get your files re-ciphered.
List of the Magniber ransomware extensions:| .lwofcre | .vbdrj | .ldfieqd | .lwvzstz | .lsjsmefxf | .flpywsghp | .pkruukfc |
| .efmbegjf | .yyqiidt | .orrnqhk | .xoanjnlp | .eenaeca | .ukijuvj | .voodpuzqw |
| .fufmhxz | .mrjgzzvk | .yszvxcht | .mqpdbn | .fbuvkngy | .rrayefq | .fdqrtqg |
| .ozyvjwiq | .qooxnfg | .cjziuvtfn | .dxjay | .vdaejaua | .vpkrzajx | .hlfvwniv |
| .zpvsxus | .fmojmiwpj | .duezepv | .xwnxyiudp | .apgfaicep | .aaovsto | .wzxjwxf |
| .eskbpuqh | .rbyqguce | .czqlxnrz | .iqqdisei | .hhremcbz | .tyvarkuq | .kgpvwnr |
| .fjckfytw | .tjtwhzx | .xbggvkiw | .ihsdj | .dbbyzwv | .jyghobr | .mftzmxqo |
| .zgsubwuw | .wchsiayw | .ukfmwlsc | .dlenggrl | .uyutiqh | .jbumkhowu | .fcldgqgi |
| .dhfjsbrz | .mjzqagq | .qspvdrq | .wlpxybe | .wbtuwonlw | .gyfrpmwt | .sjrlwwoyk |
| .kgiiyvj | .yiqmwwgi | .bbersgae | .jolpjzpj | .pghenmwaf | .xrjiflj | .fzgewejg |
| .sbfsppos | .tuzwktl | .kqgoinml | .fronstd | .rlcxhia | .dikqiqclk | .ehrdchvtb |
| .wmfxdqz | .wyhciyr | .pytgvaj | .vfmdndg | .djjzwagsy | .glmyaopcr | .uvwhyhilt |
| .fdbetowe | .indfrrr | .ksestcire | .kkxihdtg | .erkzdant | .uvomapllm | .anyxahef |
| .emrthbf | .bvvtyxrrq | .sddbixgl | .grgvzrk | .utzpcoe | .eicanuksx | .vdbhiex |
| .hdhhbmq | .jwfrghed | .okfexqp | .oiscsmw | .hlfvwniv | .elkkjjbu | .mbqxyxti |
| .mdtmhukos | .recnejqwj | .rnkzzcxqa | .fprgbk | .mpkwihqt | .ajyasmedl | .wpmvwgpn |
| .lxhytwdp | .hihxhgx | .bdpxlnurb | .rchqvsmh | .cwmnocoq | .asrmqrlq | .dguenvm |
| .pwwxmfzc | .zibunqqs | .hbcujria | .zdotwsekh | .dhtjsliq | .tcpxwmgm | .knbgbnsy |
| .jprivzfdr | .ckvqdjy | .juuscefpz | .xhspythxn | .zwtnfhjp | .zvekdkzfs | .fytmjctri |
| .ktdnjibt | .nhsajfee | .hesmsesm | .tkcmcparz | .vfmdndg | .lxxmlxfva | .qmdjtc |
| .uefktqyv | .aksxyur | .lrhcvva | .demffue | .plqapfmnu | .ywavhsk | .mpkddbfa |
| .vuwvopzm | .jiitozip | .vqcixrpu | .ebqpegds | .damdzv | .jtorauup | .erfzgwnt |
| .nktqanpg | .axlgsbrms | .xgjihjggs | .ypkwwmd | .ztppsluei | .tquadit | .wiwsvgrfy |
| .ehrdchvtb | .qzffmcofd | .skvtb | .vkcgyak | .vldrzho | .beqcerma | .zzieogce |
| .npxnjpk | .ujwkjcpx | .yksanafx | .tfgwinrhw | .igakzmgp | .cojymfvs | .dpgproeul |
| .bicdzxf | .biqwysf | .lanlaor | .otzksbpr | .jovrghlyz | .tjgmykb | .zsymadx |
| .kyhbmtmxr | .gjvbndgd | .zibunqqs | .mbfskov | .mlwzuufcg | .hqzserk | .adaxhycds |
| .mxmhkhojb | .ucykvfkiq | .ppziqprqw | .fuivmuio | .dfteeeh | .ndpyhss | .yujsgyf |