Ryuk Ransomware
April 18, 2023
Ryuk is a sophisticated ransomware program that, once deployed, encrypts files on an infected system. It targets large enterprises, hospitals, government agencies, and other organizations that use Microsoft Windows. Ryuk was first spotted in 2018. It differs in that it uses a manual hacking method and open-source tools. This allows operators to move horizontally across private networks and gain administrative access to more systems before they start encrypting the files. Ransom is usually required in bitcoins or another cryptocurrency. The name "Ryuk" comes from a character in the famous detective manga and anime Death Note from the early 2000s.
How does it work?
Ryuk is one of the first ransomware programs to identify and encrypt network drives and resources and remove shadow copies. This way, attackers can disable Windows system restore for users, making it impossible to recover from an attack. Unless, of course, you had external backups or fallback technology.
Ryuk spreads mainly via TrickBot or after a Trojan infection. However, a TrickBot condition does not always result in Ryuk. Sometimes it can take weeks after a TrickBot infection before Ryuk appears. This may be because attackers use the data collected by TrickBot to find potentially valuable information on the network, before launching the Ryuk. Unfortunately, this is also when they are hacking the rest of the network and leaking data using spyware. The targeting process involves manual hacking, which includes network reconnaissance and horizontal movement through the network. This compromises domain controllers and gains access to as many systems as possible. In this way, Ryuk's deployment process will be as fast as possible, and the damage will spread widely across the network. This will likely push the organization to act immediately rather than holding a few of its endpoints hostage.
Methods of delivery Ryuk
Like most malware, the primary delivery method is email spam (malspam). Often such emails are sent from a fake address, so the sender's name is not suspicious. However, hackers may use direct access to the insecure RDP port. The attack starts when a user opens an infected document (most often a Microsoft Office file) attached to a phishing email. This triggers the malicious macro to execute a PowerShell command that attempts to download the Emotet banking Trojan. The Trojan, in turn, downloads additional malware on the infected machine, which extracts and runs Trickbot. Its primary payload is spyware, which collects administrator credentials and allows attackers to move laterally to critical assets connected to the network. The attack chain is completed when the attackers launch Ryuk on these assets.
New Ryuk
In January 2021, a brand new version of Ryuk was discovered. Although new variants had appeared before, this particular one had a significant impact because it had the capabilities of a "classic" virus. This allowed it to spread automatically in infected networks. Because previous versions of Ryuk could not automatically move horizontally across networks, they required a dropper and manual movement. The new version of Ryuk spreads its copies from device to device without human intervention.
Encryption
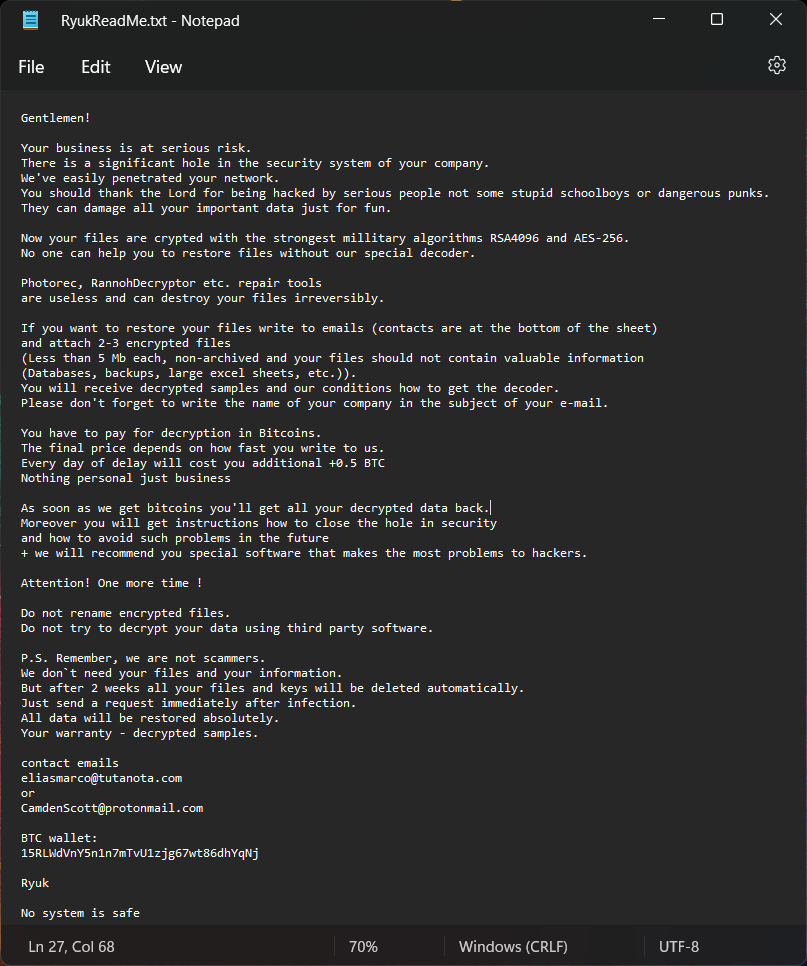
Ryuk uses a combination of encryption algorithms. It includes a symmetric algorithm - AES-256 - and an asymmetric RSA 4096. The ransomware encrypts the file using the symmetric algorithm, then consists of a copy of the symmetric encryption key, which is encrypted with the RSA public key. After paying the ransom, the Ryuk operator provides a copy of the corresponding RSA private key, which allows the decryption of the symmetric encryption key and the encrypted files.
Ransomware poses a severe threat to the stability of an infected system because it can accidentally encrypt system-critical files. Ryuk intentionally avoids encrypting certain file types (including .exe and .dll) and files in specific folders on the system. While this is not foolproof, it reduces the chances that Ryuk will break the infected computer, making it harder or impossible to retrieve the files in case of a ransom payment.
Since no publicly available tool can decrypt Ryuk's files without paying a ransom, attackers are not shy about asking for huge sums. Thus, the average ransom demand has reached $111,605. However, researchers warn that the decryptor the attackers provide can sometimes corrupt files even if paid. This usually happens with large files, where Ryuk performs only partial encryption to save time. Likewise, to prevent data recovery by alternative means, Ryuk tries to delete Volume Shadow Copy. It also contains a kill.bat script that disables various services, such as network backup and Windows Defender.
Who is behind it?
Security researchers discovered a link between the Ryuk and Hermes ransomware strains early on because of the similarities in their code and structures. Because of this, many have suggested that Ryuk may also be linked to the Lazarus Group. This is the same North Korean APT group that previously ran the Hermes ransomware. However, the code similarities alone are insufficient to assert links between Ryuk and North Korea. Hermes is a suite of ransomware that is sold on the Darknet. This makes it available for use by other cybercriminals in their attack campaigns. There was also some similarity between Ryuk and Bitpaymer Ransomware. The similarity of the ransom notes may indicate that the text may have been borrowed from Bitpaymer. According to a separate study by cybersecurity experts from various research groups the gang behind Ryuk could be of Russian origin and not necessarily state-sponsored. Thus, the Ryuk ransomware can be attributed to two criminal organizations: Wizard Spider and CryptoTech.
Ryuk's famous attacks
Ryuk ransomware attacks follow a standard pattern. Large public or private organizations are targeted and hit with raid-like attacks. Ryuk attacks have targeted targets in the United States, the United Kingdom, Germany, Spain, France, and Australia. In addition, an analysis of bitcoin transactions was conducted in early 2021. According to that report, Ryuk hackers could fraudulently obtain more than $150 million in ransom payments. The most notable Ryuk ransomware attacks have hit municipalities, school systems, technology and energy companies, and hospitals.
- December 2018: U.S. media using Tribune Publishing software, including the LA Times and West Coast publications The Wall Street Journal and the New York Times, were affected. The target of the attack: disabling infrastructure.
- March 2019: The entire Jackson County, Georgia, municipal network, except for emergency services, was shut down. Ransom amount: $400,000.
- June 2019: Riviera Beach and Lake City, Florida, were attacked weeks apart. Emergency services, pump stations, and administrative systems were affected. Ransom amounts: $600,000 and $460,000, respectively.
- July 2019: La Porte County, Indiana, paid $130,000 to get its systems back up and running.
- July 2019: New Bedford, Massachusetts, demanded $5.3 million for an IT system. Instead, the city offered the hackers $400,000, which was rejected, so they had to recover the data themselves.
- December 2019: More than 700 government agencies in Spain were attacked simultaneously. It disrupted hundreds of thousands of citizens' appointments and access to the Public Employment Service portal.
- January 2020: Electronic Warfare Associates (EWA) was attacked. The company tried to hide the data leak. However, the story broke when someone accidentally found encrypted files and ransom notes in cached Google search results.
- March 2020: Epiq Global faced an attack on 80 offices around the world, blocking customers' access to critical legal documents. No ransom payment has been reported.
- September 2020: more than 250 Universal Health Services (UHS) medical facilities were attacked; it cost UHS $67 million to recover from the attack.
- November 2020: when K12 Inc. was attacked, hackers gained access to a large amount of personal data and threatened to leak it. K12 confirmed that an unspecified ransom was made.
- November 2020: The Baltimore County Public School system was attacked. Although no ransom was paid, it cost the school system nearly $10 million to rebuild.
- May 2021: An attack on Norwegian energy technology company Volue, water and wastewater system infrastructure in more than 200 Norwegian municipalities was affected. Nearly 85% of the country's population was affected by the attack.
- June 2021: Liège, Belgium's third-largest city, attacked its IT network and services. This disrupted administrative services related to identity cards, passports and marriage appointments, births, and residence permits.
How to Remove?
If you suspect that Ryuk has infiltrated your company's computers using Emotet, you need to take action. First, if the computers are connected to the network, disconnect them. Then, after isolation, clean up the infected system(s). But that's not over yet. Because Emotet spreads through your network, a clean computer can be reinfected when it reconnects to an infected network. However, because Ryuk is quite challenging to remove, this should be handled by experienced IT professionals. Removing Ryuk in Safe Mode or through system restore is also possible. However, even if you remove Ryuk, the files will still be encrypted. To restore, you need a recovery key, which only intruders have.
How to protect yourself from Ryuk
As we noted earlier, Ryuk, like other common ransomware, is often deployed using phishing emails. Phishing can be very elaborate, and even experienced cyber experts cannot always detect it. Ensure you're using advanced email and other collaboration tools to protect against phishing and malware. But ideally, the focus should be on attack prevention. It's essential to pay attention to training employees on how to avoid phishing threats. Every employee should keep a close eye out for phishing emails. Don't click on suspicious links in your inbox. Most importantly, organizations should establish the proper cybersecurity protocol, strategy, and training program.
An AI-based endpoint protection platform that detects and prevents threats is essential to protect your enterprise from attacks. Advanced cybersecurity software can analyze and triage threats based on an intimate knowledge of your environment. Furthermore, it can conduct a thorough investigation to develop malware. When choosing a defense solution, use a detection mechanism independent of attacks. Such a mechanism can protect against previously unknown Ryuk variants as they emerge. In addition, since Ryuk looks for the weakest link in the chain, it is highly recommended that you continually scan your network and systems for security vulnerabilities and fix them as soon as they are discovered.