BlackBerry experts haber descubierto an unusual multi-platform (for Windows and Linux) ransomware Tycoon. It is written in Java and uses JIMAGE image files to avoid detection.
Researchers believe Tycoon was used for targeted and very rare attacks, in favor of this theory says number of victims and applied delivery mechanism. De este modo, the ransomware was clearly intended to attack small and medium-sized enterprises, as well as educational institutions and software developers.
“The use of Java and JIMAGE are unique. Java is very rarely used to write malware for endpoints, since Java Runtime Environment is required to execute the code. Image files are also rarely used for malware attacks”, — say BlackBerry experts.
En este caso, the attack begins quite normally: the initial compromise is carried out through unsafe RDP servers that are «visible» desde Internet. Sin embargo, the investigation showed that the attackers then use Image File Execution Options (IFEO) inyección to ensure a stable presence in the system, launch a backdoor along with the Microsoft Windows On-Screen Keyboard (OSK), and disable anti-virus products using ProcessHacker.
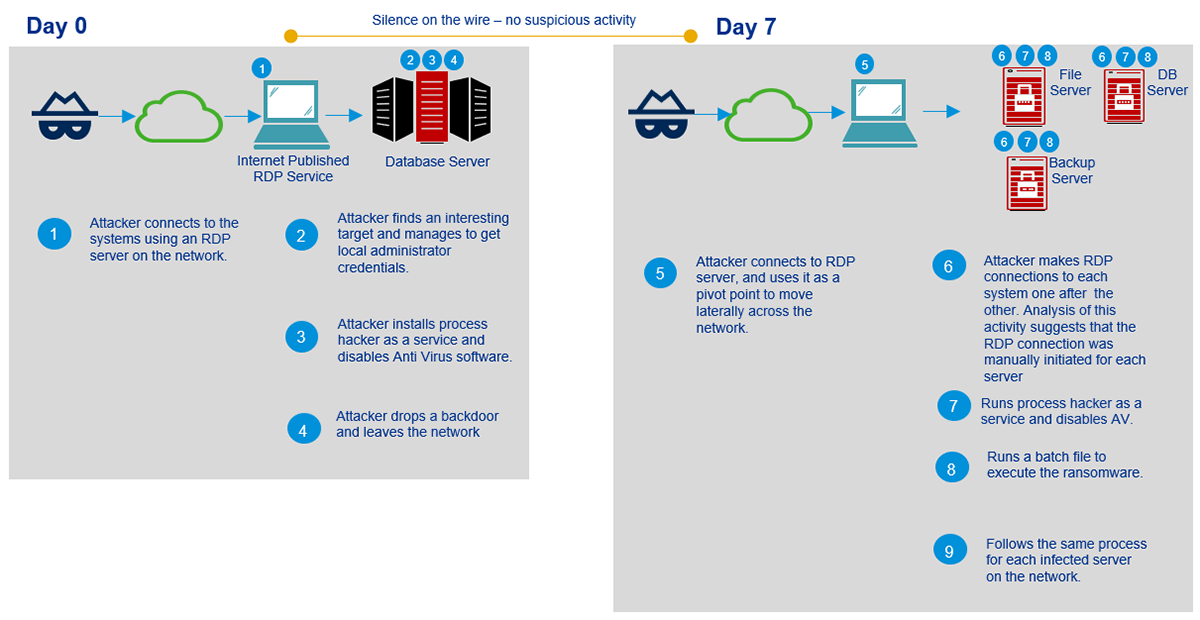
Having gained a foothold in the company’s network, attackers launch a ransomware module in Java that encrypts all file servers connected to the network, including backup systems.
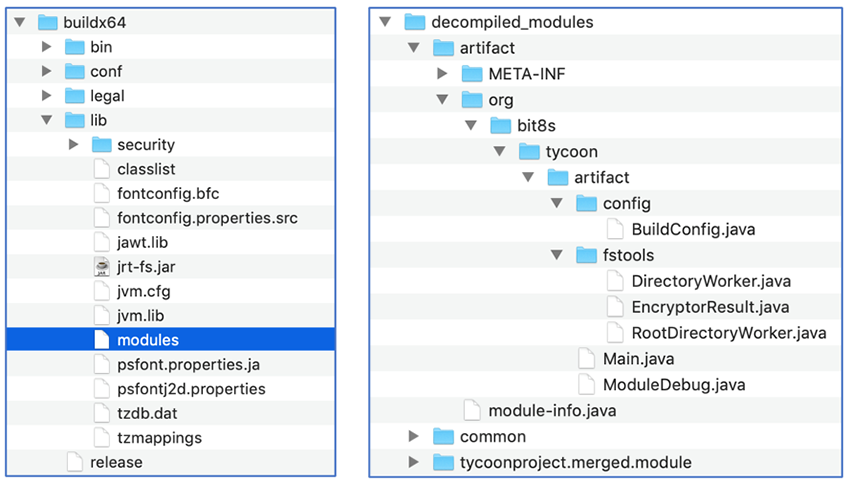
The encryptor itself is deployed from a ZIP archive containing a malicious Java Runtime Environment (JRE) assembly and a compiled JIMAGE image. This file format is typically used to store custom JRE images and is used by the Java Virtual Machine. Researchers note that this file format, first introduced along with Java 9, is poorly documented and developers overall rarely use it.
It is also noted that Tycoon deletes the source files after encryption, and overwrites them to accurately prevent information recovery. For this task is used the standard Windows utility cipher.ex. Además, during encryption, the malware skips parts of large files to speed up the process, which leads to damage of these files and inability to use them.
Además, each file is encrypted using a new AES key. The ransomware uses the asymmetric RSA algorithm to encrypt the generated AES keys, eso es, to decrypt the information, a private attacker RSA key is required.
"Sin embargo, one of the victims who asked for help on the Bleeping Computer forum published an RSA private key, allegedly obtained from the decryptor, which the victim acquired from the attackers. This key worked successfully to decrypt some files affected by the earliest version of Tycoon ransomware, which added the .redrum extension to encrypted files”, — write the experts, but warn that, desafortunadamente, for encrypted files with the .grinch and .thanos extensions, this tactics no longer work.
The researchers also identified a possible link between Tycoon and the Dharma/CrySIS ransomware, cual, por ejemplo, also spread through infected pdf files. Their theory is based on the coincidence of email addresses, the similarity of texts from notes with a ransom demand, as well as the coincidence in the names that are assigned to encrypted files.
Interestingly that MyKingz botnet uses not exotic picture formats, pero, por ejemplo, Taylor Swift to infect target machines.

