Expertos de la empresa Gemini Advisory publicó un informe, según el cual en foros clandestinos de hackers se encontraron dos precedentes, cuando los piratas informáticos recopilaron datos de tarjetas EMV y pusieron esta información a la venta. De este modo, ataques a tarjetas EMV, que eran solo una teoría 12 años, han sido notados en la realidad.
El Publicación ZDNet dice que recientemente los analistas de Cyber R&D Lab realizó un interesante experimento relacionado con tarjetas EMV.
Los investigadores emitieron tarjetas EMV con un chip en 11 bancos en estados unidos, Reino Unido y UE, y luego usó herramientas de piratería contra ellos, que generalmente se utilizan para copiar información almacenada en tarjetas EMV y sus bandas magnéticas.
Como resultado, Los investigadores pudieron extraer datos de tarjetas EMV y crearon clones con la misma banda magnética., pero sin el chip real.
“Esto fue posible gracias al hecho de que todas las tarjetas EMV tienen una banda magnética por si acaso., por ejemplo, para una situación en la que un usuario ha viajado al extranjero y no puede utilizar EMV, o hay un antiguo terminal PoS”, – dijo a los periodistas de ZDNet.
El hecho de que es posible copiar la banda magnética de las tarjetas EMV se sabe desde hace 2008, pero se creía que era difícil abusar de esta característica, ya que los bancos planeaban transferir a todos los usuarios a EMV y a menudo se negaban a utilizar bandas magnéticas. Como lo ha demostrado la práctica, esto no sucedió, y Ciber R&Los especialistas de D Labs informaron que lograron clonar cuatro tarjetas de la forma descrita anteriormente y realizar transacciones.
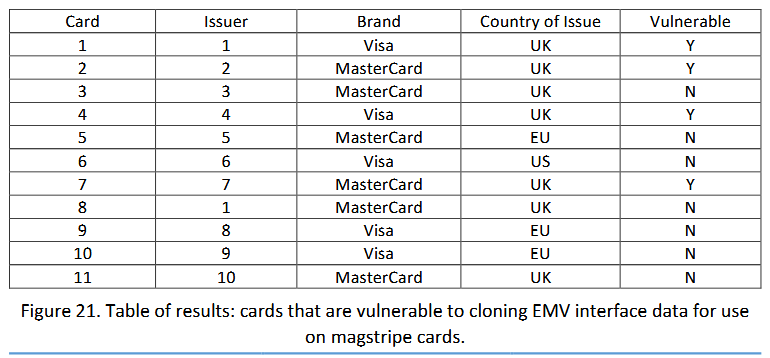
Sin embargo, hasta esta semana, el problema todavía se consideraba bastante teórico, ya que no se conocía sobre el uso masivo de esta técnica por parte de hackers, y ahora los expertos de Gemini Advisory han descubierto tales precedentes.
Los investigadores escriben que los datos de las tarjetas EMV fueron robados de la cadena de supermercados estadounidense Key Food Stores Co-Operative Inc., así como de la licorería americana Mega Package Store.
El hecho de que los delincuentes hayan comenzado a clonar tarjetas EMV parece confirmado por la advertencia, emitido por Visa. Los representantes de Visa escriben que malware como Alina POS, Dexter POS y TinyLoader se han actualizado y ahora pueden recopilar información de tarjetas EMV, que nunca antes se había visto, ya que los datos recopilados de esta manera generalmente no se pueden monetizar.
Gemini Advisory cree que el método que empezaron a utilizar los delincuentes fue descrito ya en 2008, y que esta técnica, Clonación de derivación EMV, fue objeto de una investigación reciente realizada por Cyber R&Laboratorios D.
“Demostré la clonación de datos de chip a banda magnética, pero los bancos dijeron que las tarjetas emitidas después 2008 no sería vulnerable y los datos del chip serían “inútiles para el estafador”. Esta nueva investigación muestra que el problema aún no se ha solucionado, 12 años después”, – dicho ingeniero steven murdoch, quien describió la técnica de clonación en 2008.
En teoria, No es demasiado difícil defenderse de tales ataques.: basta con que los bancos realicen controles más exhaustivos al procesar transacciones con bandas magnéticas de tarjetas EMV. Sin embargo, desafortunadamente, como estudio de Cyber R&D Labs ha demostrado, No todos los bancos prestan atención a esto..
A propósito, aquí el hacker tamagotchi recaudó instantáneamente en Kickstarter una cantidad 7 veces más de lo necesario – El hacking está de moda., y tus datos personales, incluyendo cuentas bancarias y tarjetas, siempre esta en peligro. Déjame recordarte también que El troyano BlackRock roba contraseñas y datos de tarjetas de 337 aplicaciones en el sistema operativo Android.

