Investigadores de ThreatFabric han publicado un informe sobre el estudio de un nuevo troyano en el sistema operativo Android, llamado roca negra. Este malware tiene como objetivo robar datos de varias aplicaciones., incluyendo aplicaciones de citas, mensajería instantánea, productos bancarios, redes sociales y demás. En total, el troyano puede atacar 337 aplicaciones.
Esta amenaza se notó por primera vez en mayo de este año., pero sus raíces en BlackRock van mucho más allá. El caso es que el troyano se basa en los códigos fuente “filtrados” de otro malware, Jerjes, cual, a su vez, también se basó en las fuentes de otro malware.
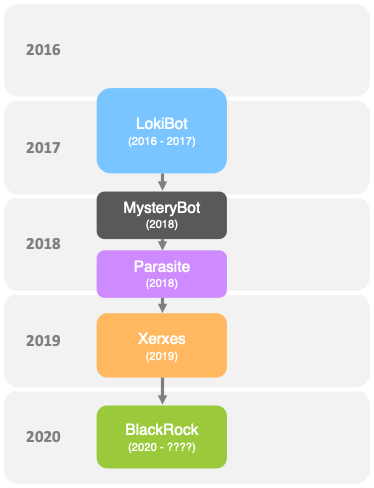
Cabe señalar que a BlackRock se le agregaron nuevas funciones., en particular diseñado para robar contraseñas de usuarios e información de tarjetas bancarias.
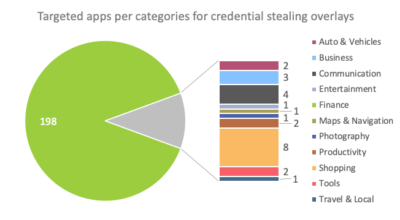
En general, BlackRock funciona de la misma manera que la mayoría de los demás banqueros de Android; solo apunta a más aplicaciones. Así que, el troyano roba las credenciales de los usuarios, pero si es posible, solicita a la víctima que ingrese la información de la tarjeta de pago (si la aplicación de destino admite transacciones financieras).
“La recopilación y el robo de datos se realiza mediante superposiciones. Eso es, El malware detecta cuando un usuario intenta interactuar con cualquier aplicación legítima y muestra su propia aplicación falsa en la parte superior de esta ventana., donde la víctima ingresa sus credenciales o datos de la tarjeta», – escrito por especialistas de ThreatFabric.
Para poder mostrar dichas ventanas encima de otras aplicaciones, el troyano utiliza un viejo truco y solicita al usuario acceso al Servicio de Accesibilidad. Habiendo recibido estos derechos, el malware se otorga a sí mismo otros permisos necesarios, y luego obtiene completamente acceso de administrador en el dispositivo usando Android DPC.
Los investigadores de ThreatFabric escriben que la mayoría de las superposiciones de BlackRock están diseñadas para atacar aplicaciones financieras y redes sociales.. Sin embargo, hay superposiciones para otro tipo de aplicaciones, incluyendo citas, noticias, compras y así sucesivamente. Puede encontrar una lista completa de aplicaciones específicas en el informe de expertos..
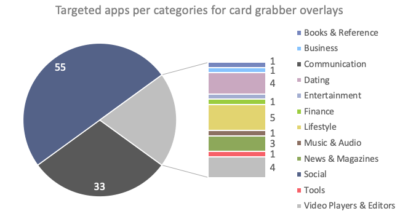
Además de imponer superposiciones de phishing, el troyano puede realizar otras operaciones maliciosas:
- interceptar mensajes SMS;
- utilizar inundación de SMS;
- spam a todos los contactos con SMS predefinidos;
- ejecutar aplicaciones específicas;
- interceptar clics (registrador de teclas);
- mostrar notificaciones push;
- sabotear el funcionamiento de aplicaciones antivirus.
BlackRock se está propagando actualmente a través de sitios fraudulentos que se disfrazan de paquetes de actualización falsos de Google.. Hasta que se encontró el troyano en la tienda oficial de Google Play Store.
Déjame recordarte que recientemente escribí sobre dos nuevos programas maliciosos, que puede robar cookies de aplicaciones de Android.

