Especialistas de la Agencia de Ciberseguridad y Protección de Infraestructura, organizado por el Departamento de Seguridad Nacional de EE.UU. (DHS CISA), prevenido about growth of activity of LokiBot infostealer aka Loki and Loki PWS; not to be confused with the Trojan of the same name for Android), which has been increasing since July this year.
ZDNet journalists nota that Malwarebytes experts also drew attention to the surge in LokiBot activity, confirming the findings of CISA specialists.
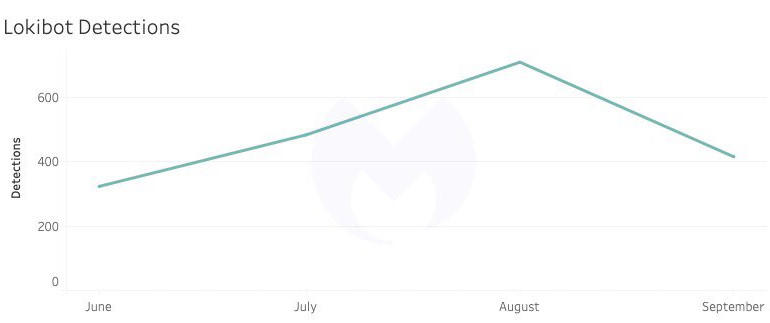
LokiBot is one of the most dangerous infostealers at the moment. The Trojan has been known to cybersecurity experts since the mid-2010s.
Durante muchos años, its source code was distributed on hacker forums completely free of charge, which made LokiBot one of the most popular password stealing tools (mainly among low and medium-skilled cybercriminals).
Actualmente, several hack groups actively use malware at once, spreading it using a variety of methods, from email spam to hacked installers and malicious torrent files.
“By infecting victims’ ordenadores, LokiBot focuses on finding locally installed applications and retrieving credentials from their internal databases. Por ejemplo, LokiBot steals data from browsers, clientes de correo electrónico, FTP applications and cryptocurrency wallets”, – inform DHS CISA researchers.
Today LokiBot is no longer just an info-stealer, but a more complex threat. De este modo, the malware is equipped with a keylogger that intercepts keystrokes in real time (in order to steal passwords that are not always stored in the internal database of the browser), and a utility for creating screenshots (usually used to capture documents after they have been opened on a computer victims). Además, LokiBot also acts as backdoor, allowing hackers to launch other malware on infected hosts.
The data stolen by LokiBot usually ends up on underground marketplaces. Según KELA analysts, LokiBot is one of the main providers of credentials for the Genesis marketplace.
En 2019, SpamHaus experts named LokiBot the malware with the most active command servers, Any.Run experts placed LokiBot in 4th place in the ranking of the most common threats in 2019, and in the SpamHaus ranking for the first half of 2020, LokiBot confidently occupies second place.

