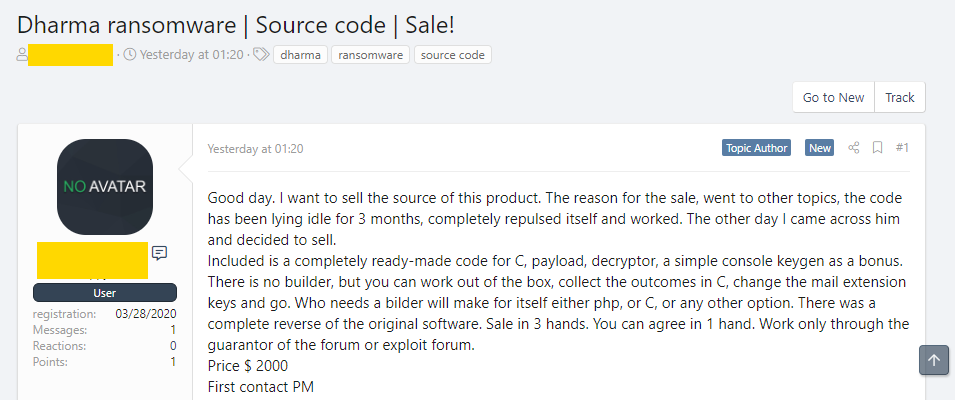
ZDNet informes que el código fuente de uno de los ransomware más rentables de nuestro tiempo, el ransomware Dharma, se puso a la venta en dos foros de hackers el fin de semana pasado. Las fuentes se venden por $2,000.
Permítanme recordarles que este año el FBI calificó a Dharma como el segundo ransomware más rentable de los últimos años durante su informe en la conferencia y RSA.. Por lo tanto, desde noviembre 2016 a noviembre 2019, operadores de ransomware recibidos $24 millón en rescate de sus víctimas.
El ransomware más peligroso del año pasado, Recuerdo, se llamaba Emotet.
“Es probable que la venta actual del Código del Dharma pronto resulte en una filtración al público.. Eso es, el malware estará disponible para un público más amplio. Éste, a su vez, conducirá a una amplia distribución del código fuente entre muchos grupos de hackers, Y esto, en última instancia, será seguido por una oleada de ataques”., – ZDNet cita a un experto anónimo en seguridad de la información.
Sin embargo, El jefe del departamento de ciberinteligencia de McAfee dijo a ZDNet que el código Dharma ha estado circulando entre los piratas informáticos durante mucho tiempo., y ahora acaba de llegar a los foros públicos.
Al mismo tiempo, el experto expresó la esperanza de que tarde o temprano el código fuente caiga en manos de especialistas en seguridad de la información, y esto ayudará a identificar las deficiencias del malware y crear decodificadores.
“El Dharma existe desde 2016, y el ransomware subyacente a este malware se llamaba originalmente CrySiS. Funcionó en Ransomware-as-a-Service (RaaS) esquema, eso es, otros delincuentes podrían crear sus propias versiones de malware para distribuir, generalmente a través de campañas de spam, kits de explotación, o fuerza bruta RDP”, – destacados reporteros de ZDNet.
Al final de 2016, un usuario con el apodo crss7777 al corriente en los foros de Bleeping Computer hay un enlace a Pastebin que contiene claves maestras del cifrador CrySiS, cual, como establecieron más tarde los expertos, eran genuinos. Después de eso, CrySiS dejó de existir, “renacer” como Dharma.
Aunque las claves del Dharma corrieron la misma suerte en 2017, Esta vez los operadores de ransomware no cambiaron de nombre y continuaron trabajando., eventualmente convirtiendo su RaaS en uno de los ransomware más populares del mercado.
"Entonces, en años recientes, Dharma recibe actualizaciones periódicamente. Por ejemplo, en 2018 y 2019, La clandestinidad criminal se adaptó a las nuevas tendencias y pasó de la distribución masiva de ransomware a través del correo no deseado a ataques dirigidos a redes corporativas.. Lo mismo hicieron los operadores del Dharma.», – dice la publicación ZDNet.
Cabe señalar que en la primavera de 2019, una nueva cepa de ransomware Phobos apareció en la red, utilizado principalmente para ataques dirigidos. Investigadores de Coveware y Malwarebytes He notado que es casi idéntico al Dharma.. Sin embargo, al mismo tiempo, Dharma no dejó de existir y siguió trabajando en paralelo con Fobos. Por ejemplo, Expertos de avast observó tres nuevas versiones del Dharma la semana pasada.

