Recientemente, la plataforma gitlab realizó una auditoría de seguridad, Análisis de si trabajar desde los empleados en casa es resistente a los ataques de phishing. Como se vio despues, Cada quinto se puso en phishing en Gitlab: 20% de los empleados acordaron ingresar sus credenciales en una página de inicio de sesión falsa.
Un ataque de entrenamiento realizado por el equipo rojo de Gitlab simuló una verdadera campaña de phishing, cuyo propósito era averiguar las credenciales de los empleados de Gitlab. Para este propósito, Los especialistas en seguridad de la información registraron el nombre de dominio gitlab.company y lo configuraron para enviar correos electrónicos de phishing utilizando el código abierto Fomento y gsuite de Google. Los correos electrónicos de phishing fueron diseñados para simular notificaciones reales del departamento de TI, supuestamente informando sobre la necesidad de actualizar la computadora portátil.
«Se les pidió a los usuarios objetivo que hicieran clic en el enlace, supuestamente para aceptar la actualización, Pero, de hecho, este enlace condujo a una página de inicio de sesión falsa en gitlab.com ubicada en el dominio gitlab.company», - Digamos en Gitlab.
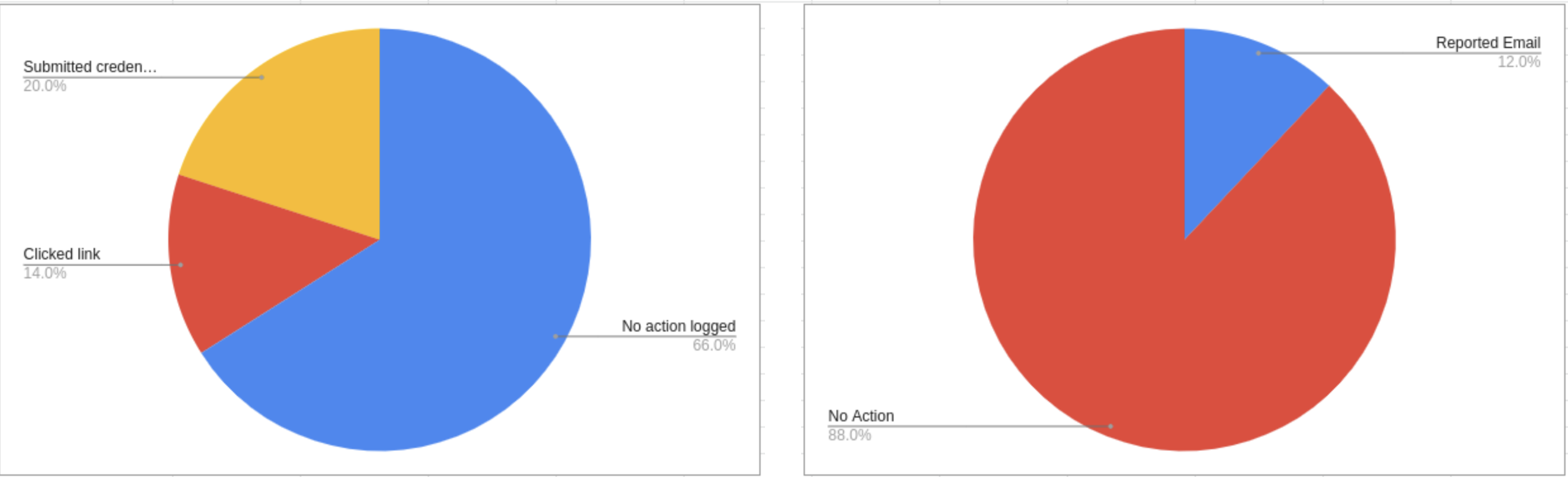
Durante la auditoría fueron enviadas 50 Tales correos electrónicos. Como resultado, 17 (34%) de los destinatarios hacer clic en el enlace del mensaje, ir a un sitio especial de phishing. De estos, otro 10 gente (59% de los que fueron al sitio, y 20% del grupo total probado) continuó trabajando e ingresó sus credenciales en una página falsa. Sin embargo, solamente 6 fuera de 50 destinatarios de mensajes de phishing (12%) informó un intento de phishing de Gitlab Security Staff.
Vale la pena decir que, Según Verizon's informe, 22% del número total de incidentes relacionados con la divulgación de datos generalmente relacionados con el phishing, y sobre 90% de los incidentes están relacionados con la interacción social. El informe también establece que en promedio, La frecuencia de los clics en los enlaces de phishing debe ser mucho menor – 3.4% contra 20% Mostrado por los empleados de Gitlab.
Otra empresa de seguridad de la información, rápido7, escribió que la frecuencia de los clics en los enlaces en los correos electrónicos de phishing varía de 7 a 45%. Otro 2018 informe, Compilado por KnowBe4, establece que el porcentaje promedio de trabajadores vulnerables a los ataques de phishing en diversas industrias es 27%.
De acuerdo con la Informe Secure de Vade, durante la pandemia, aumentó el número de ataques de phishing usando Facebook por 358.8%, y usar Whatsapp Messenger – por 13467%.
Vicepresidente de Seguridad de Gitlab, Jonathan Hunt, le dijo al registro que generalmente está contento con los resultados de la auditoría y se complace en ver que los resultados de Gitlab son mejores que el promedio en la empresa.
"Inicialmente, el [Equipo rojo] sugirió que más personas se enamorarían de este cebo de phishing, Pero esta suposición resultó estar equivocada. Algunos proveedores afirman que la tasa de éxito promedio de los ataques de phishing se trata de 30-40%, Así que es bueno ver que nos quedamos por debajo de este nivel»
Teniendo en cuenta que la popularidad del phishing no piensa en disminuir, Hunt enfatiza que las empresas deben capacitar a sus empleados en seguridad de la información, independientemente de si trabajan de forma remota o no:
"Esto significa que las empresas, independientemente de si trabajan de forma remota o no, Debe capacitar a sus empleados para que mantengan el nivel adecuado de vigilancia al tratar con el correo electrónico. A medida que las organizaciones se mueven cada vez más al trabajo remoto y, potencialmente, puede usar servicios en la nube con mayor frecuencia, La gestión de la identidad del usuario y la autenticación multifactor se convierten en factores críticos. "
Déjame recordarte que también Github recently warned empleados y usuarios sobre el mayor peligro de ataques de phishing.

