Expertos del Proyecto Cero de Google estimar eso 11 0-vulnerabilidades del día, actively exploited by hackers, were identified in the first half of 2020.
The current number of 0-day problems indicates that, más probable, that overall this year will be identified the same number of zero-day vulnerabilities, as in 2019 (20).
The link above leads to the company’s internal statistics, which Google specialists collected and tracked since 2014. Así que, for the first half of 2020, experts included the following problems in their list.
1. Firefox (CVE-2019-17026)
The bug that received the identifier CVE-2019-17026 was discovered by experts from the Chinese company Qihoo 360, and it was associated with the work of IonMonkey – the JavaScript JIT compiler SpiderMonkey, the main component of the Firefox kernel responsible for JavaScript operations (JavaScript engine of the browser). The vulnerability has been classified as type confusion.
The patches are included with Firefox 72.0.1 and are available aquí.
2. explorador de Internet (CVE-2020-0674)
El problema was exploited by the North Korean hacker group DarkHotel, in conjunction with the aforementioned 0-day bug in the Firefox browser. Both issues have been used to track targets in China and Japan, and have been discovered by Qihoo 360 and JP-CERT experts. Victims of this campaign were redirected to a site where either a Firefox or IE vulnerability was exploited; later victims were infected with the RAT Gh0st.
The patches are included in the February «Martes de parches» and are available aquí.
3. Cromo (CVE-2020-6418)
The vulnerability was identified by experts from the Google Threat Analysis Group, but there are no details about the attacks that exploited the problem.
The bug was fixed with the release of Chrome version 80.0.3987.122, patches are available aquí.
4 y 5. Trend Micro OfficeScan (CVE-2020-8467 and CVE-2020-8468).
Trend Micro employees spotted both zero days. The bugs supposely have been discovered when Trend Micro investigated a different, older zero-day issue in the same product, used for hacking of Mitsubishi Electric.
The patches can be found aquí.
6 y 7. Firefox (CVE-2020-6819 and CVE-2020-6820)
Detailed information about the attacks that used these 0-days has not yet been published, although cybersecurity researchers speculate that these problems could be part of a chain of exploits.
Vulnerabilities are fixed in Firefox 74.0.1, patches are available aquí.
8, 9, y 10. Microsoft (CVE-2020-0938, CVE-2020-1020, and CVE-2020-1027)
Google experts found and reported about all three bugs to Microsoft engineers. As with most other Google Threat Analysis Group “discoveries”, the details of these issues are kept secret and nothing is known about the attacks. The vulnerabilities were fixed as part of the April «actualizar el martes», patches are available aquí.
11. Sophos XG Firewall (CVE 2020-12271)
Anteriormente en 2020, an unknown group of hackers descubierto and exploited this vulnerability. Later Sophos experts said that using the bug, hackers tried to deploy the Ragnarok ransomware on infected hosts, but the company said that it blocked most of the attempts.
Patches are available aquí.
Déjame recordarte que en 2019, Google specialists discovered 20 vulnerabilidades de día cero, 11 of which were found in Microsoft products.
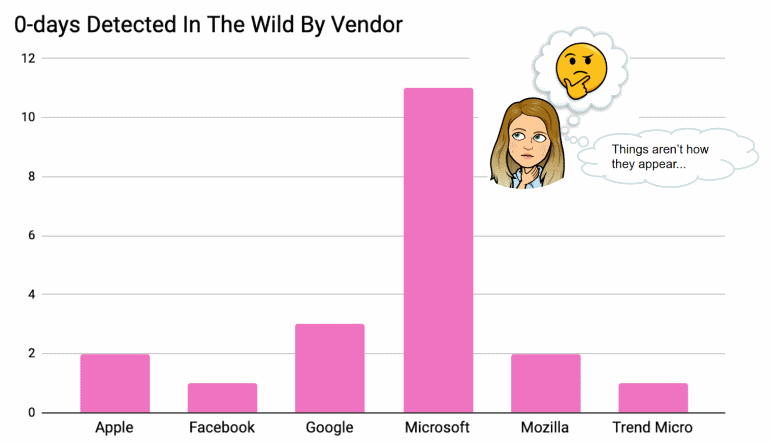
Al mismo tiempo, experts explain that Microsoft has the most bugs, as there are more security tools designed to detect bugs in Windows.

