ESET analysts prevenido about surge in the activity of the banking Trojan Grandoreiro amid COVID-19 pandemic. The bunker is distributed through fake coronavirus videos.
Experts report that Grandoreiro, previously written in Delphi, was distributed mainly through spam, through fake messages about the need to update Java or Flash.
“We have seen Grandoreiro being distributed solely through spam. The authors usually utilize a fake Java or Flash update, but recently, perhaps unsurprisingly, we have observed their spam exploiting the fear around COVID-19 as well”, – tell ESET experts.
Active since 2017, banker has been openly parasitizing on the COVID-19 pandemic: it began to hide in videos on fake sites that promise to provide users with some sensational data on coronavirus.
When you try to play a video on such a resource, malware starts downloading on the user’s device.
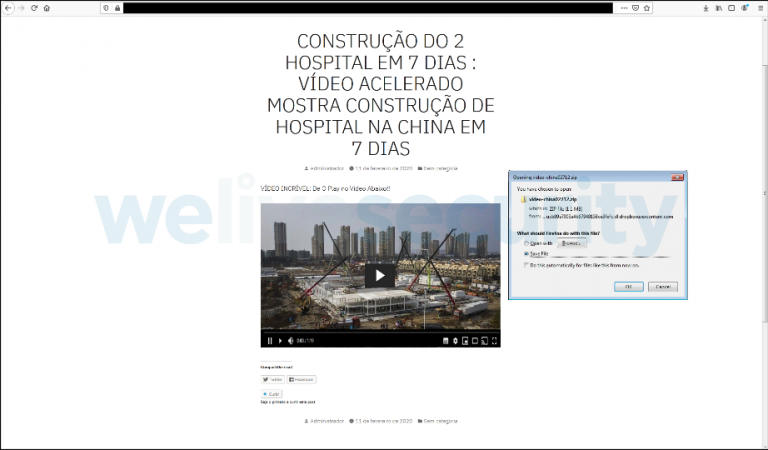
A propósito, as a result of the pandemic, intensified interest of users in pirated sites and videos, cual, por supuesto, is used by cybercriminals.
Among the functions of Grandoreiro malware are: window manipulation, self-updating, registrador de teclas, emulation of mouse and keyboard actions, victim’s browser control and navigation to selected URLs, as well as restarting devices and blocking access to certain websites.
“Interesting feature of Grandoreiro is its great effort to avoid detection. That includes many techniques to detect or even disable banking protection software. It also utilizes a very specific application of the binary padding technique we have not seen before that makes it hard to get rid of the padding while keeping a valid file”, – write ESET researchers.
The trojan collects various information about compromised devices: nombre de la computadora, nombre de usuario, version of the operating system. He finds out if the application for protecting access to online banking is installed, gets a list of installed security products.
Some versions of Grandoreiro are also capable of stealing credentials stored in Google Chrome and Microsoft Outlook.
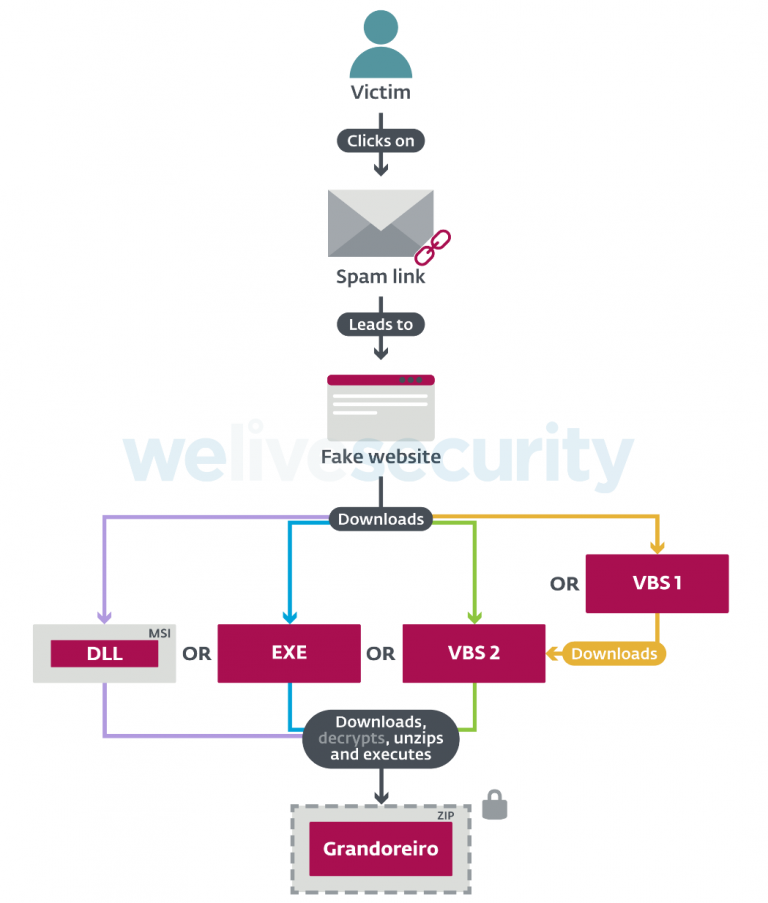
Unlike other banking trojans, Grandoreiro uses fairly small networks to spread. For different campaigns, selected different types of downloaders, which are often stored in well-known public services such as GitHub, buzón, Pastebin, 4shared or 4Sync.
Researchers note that the banker is still focused primarily on users from Latin American countries: Brasil, México, Spain and Peru.

