Expertos en Intsights encontró que recientemente en Darknet aumenta las credenciales del canal de YouTube de YouTube, y también, Como un "efecto secundario", Esto estimula las actividades de verificación de datos.
En foros y sitios de hackers que venden credenciales, Puedes encontrar más y más ofertas de este tipo.
Cabe señalar que los cibercriminales durante mucho tiempo estuvieron interesados en YouTube, porque el sitio les proporciona una nueva audiencia que se puede usar de varias maneras, De fraude a publicidad. Además, Los atacantes a menudo "roban" los canales populares de sus legítimos propietarios, y luego exige un rescate para el regreso del acceso.
"Los datos en los canales de YouTube se recopilan principalmente de computadoras infectadas con malware, Como resultado de campañas de phishing, etc.. Después de que la información robada se clasifica en inicios de sesión y contraseñas específicas de ciertos servicios, y luego se vendió en el mercado negro ", - Dicho INTSIGHTS Investigadores.
El costo de los listados en venta con datos grabados de los canales de YouTube es proporcional al número de suscriptores. Los investigadores dan algunos ejemplos. Así que, en un caso, el precio de un canal con 200,000 Los suscriptores comenzaron en $1,000 y aumentado en incrementos de $200.
En otro caso, Los investigadores encontraron un anuncio de subasta, en el que vendieron datos de 990,000 canales activos, Y el precio comenzó en $1,500 (el que pagó $2,500 recibió una lista sin ofertar). Obviamente, El vendedor esperaba ganar dinero rápidamente vendiendo los datos., Como temía que sus víctimas notaran compromiso, recurrir para apoyar y recuperar el acceso a sus cuentas.
Otro conjunto de 687 Cuentas de YouTube, ordenado por el número de suscriptores, fue puesto a la venta a un precio inicial de $400 (el precio aumentó en incrementos de $100, y para $5,000 se podría retirar mucho de inmediato).
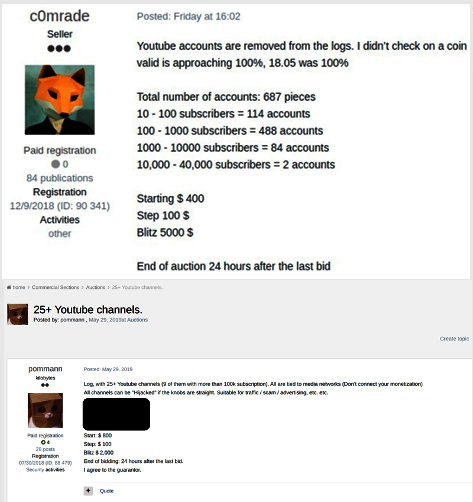
Los expertos en intsights creen que los piratas informáticos pueden recopilar material para tales listas con credenciales de los canales de YouTube, Verificar bases de datos con inicios de sesión y contraseñas robadas (En busca de datos de cuentas de Google) y datos recibidos de computadoras infectadas.
Los expertos en INTSights escriben que los ciberdelincuentes anteriores utilizaron campañas de phishing sofisticadas y kits de herramientas de proxy inverso para falsificar la autenticación de dos factores de Google. Ahora los vendedores rara vez mencionan 2FA, y lo más probable es que esto sugiera que las cuentas secuestradas no estaban protegidas por la autenticación de dos factores.
Revista de computadoras bleeping notas que los usuarios que sufrían de piratear y secuestrar una cuenta en YouTube a menudo se quejan de que los engañaban para que descargaran el malware. Por ejemplo, En la red puedes encontrar tal quejas:
“Fingieron ser patrocinadores de YouTube, y cuando intenté acceder a su sitio, Keylogger / Spyware se cargó a mi navegador. Por un máximo de un par de minutos, Cambiaron mi contraseña, eliminé mis dispositivos, eliminé mi número de teléfono y mi correo electrónico utilizado para la recuperación. Entonces intentaron extorsionarme el dinero, Querían que les enviara BTC, O venderán mi canal ".
Otra víctima de estafa dice Una historia similar Cuando los estafadores fingieron estar buscando personas para colaborar.
Por ejemplo, Te dije que La botnet MyKingz utiliza una foto de Taylor Swift para infectar las máquinas objetivo. Solo una buena foto)

