Los analistas de Microsoft han descubierto una campaña maliciosa, en el que los piratas informáticos obligan a los usuarios a resolver CAPTCHA antes de obtener acceso a contenido malicioso en un documento de Excel. Este archivo contiene macros que se instalan en las máquinas de las víctimas GraceWire Trojan, que roba información confidencial (por ejemplo, contraseñas).
La responsabilidad de esta campaña recae en el grupo de hackers Chimborazo, que los expertos han estado observando desde enero de este año.
Esta campaña se llamó Chimborazo Dudear. Inicialmente, Los piratas informáticos actuaron según el esquema clásico y aplicaron documentos Excel maliciosos a los correos electrónicos de phishing.. Luego cambiaron a enlaces incrustados en mensajes.. En semanas recientes, el grupo comenzó a enviar correos electrónicos de phishing que contenían enlaces a sitios de redireccionamiento (recursos generalmente legítimos que fueron pirateados), y, a veces, se adjunta a los correos electrónicos un archivo adjunto HTML que contiene un iframe malicioso..
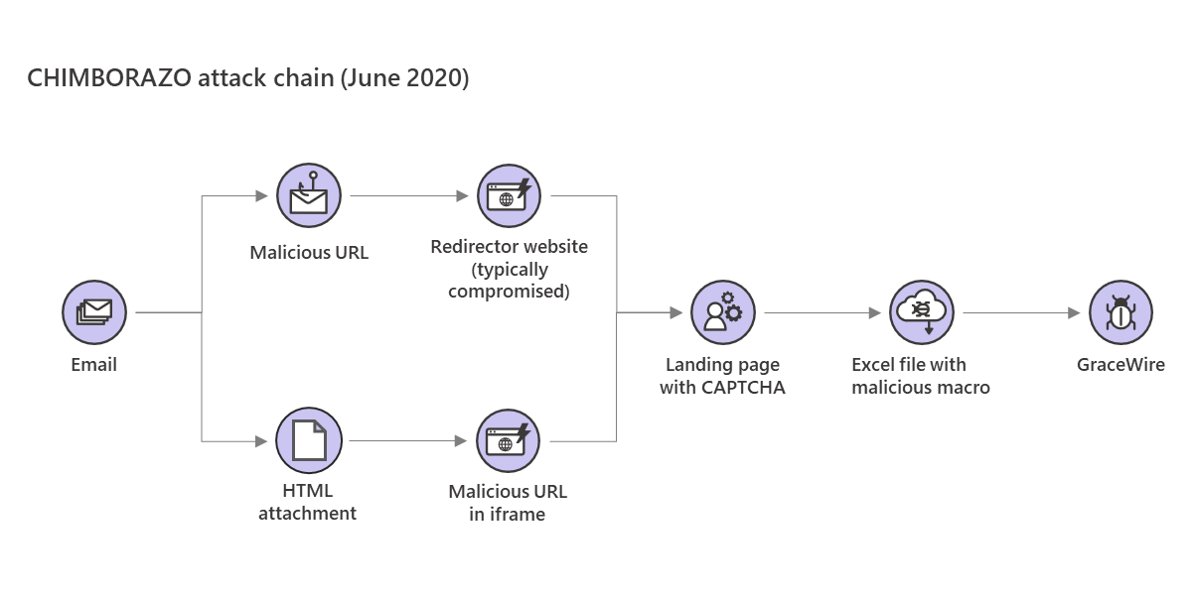
Al hacer clic en dicho enlace o abrir un archivo adjunto, En cualquier caso, la víctima será llevada al sitio con la descarga de un archivo malicioso.. Sin embargo, antes de acceder al archivo en sí, el usuario se verá obligado a resolver CAPTCHA.
De este modo, los atacantes intentaron impedir el funcionamiento de los mecanismos de defensa automáticos, que debería detectar y bloquear tales ataques. Típicamente, Este análisis se realiza mediante bots que descargan muestras de malware., ejecutarlos, y analizarlos en máquinas virtuales. CAPTCHA garantiza que una persona viva cargará la muestra de malware”., — dicen los analistas de Microsoft.
Déjame recordarte, que por cierto, 82.5% of Microsoft Exchange servers are still vulnerable.
En enero de este año, Especialistas de Inteligencia de Seguridad ya escribieron sobre los ataques del grupo Chimborazo. Luego, los investigadores dijeron que un grupo de piratas informáticos utiliza el seguimiento de direcciones IP para identificar las computadoras desde las que descargaron un archivo Excel malicioso.. Presumiblemente, Esto también se hizo para evitar la detección automática..
Experto en malwarebytes Jérôme Segura escribe que el uso de CAPTCHA por parte de piratas informáticos es un caso raro pero no sin precedentes. Por ejemplo, se refiere a un tweet de otro especialista en seguridad de la información, fechado a finales de diciembre 2019. Entonces, También se descubrió un CAPTCHA falso., que los atacantes utilizaron con éxito para complicar el trabajo de análisis automático.
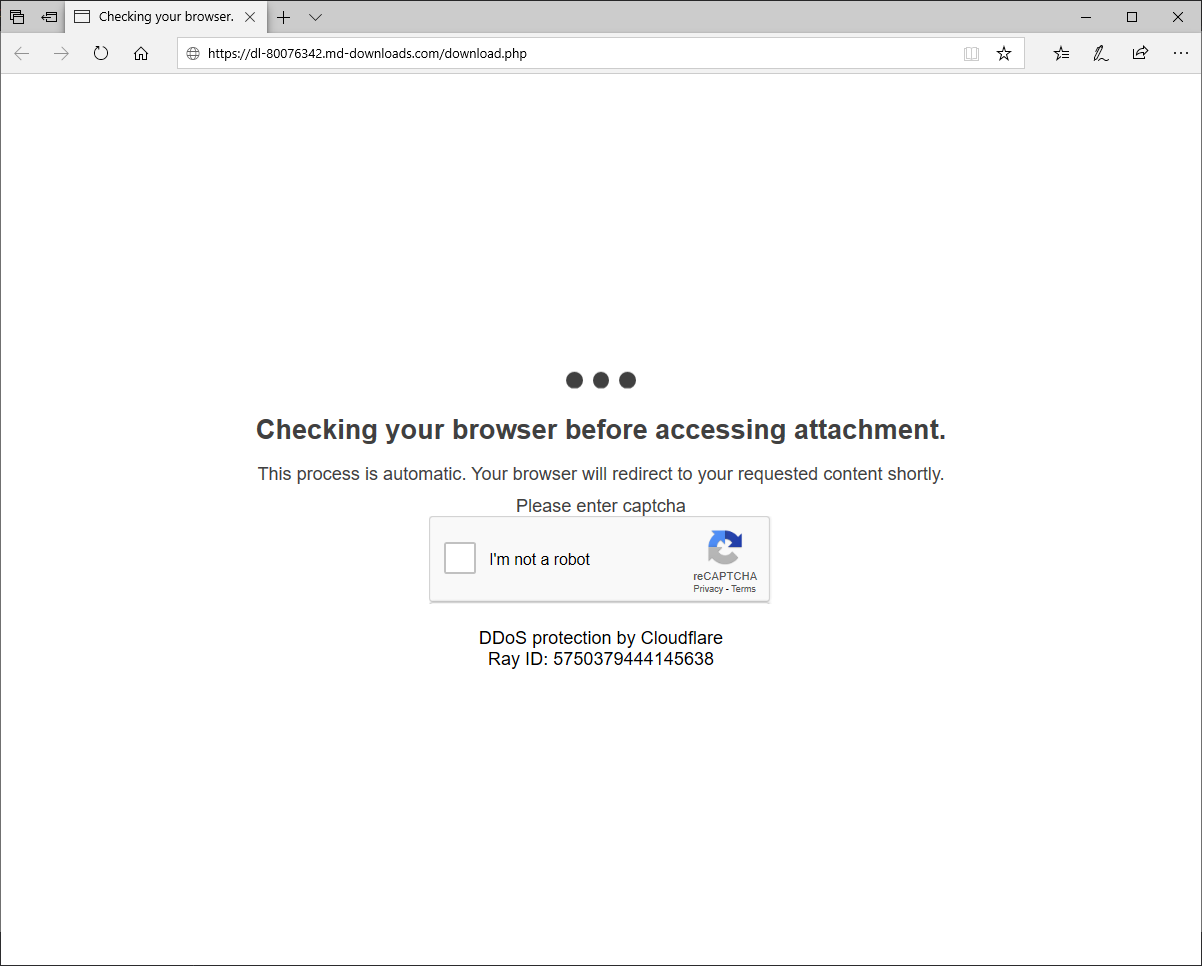
CAPTCHA descubierto por Microsoft también puede ser falso. Como puedes ver en la imagen de arriba., el sitio del atacante afirma utilizar reCAPTCHA, pero a continuación se afirma que Cloudflare brinda protección contra ataques DDoS. Estos son dos servicios separados., aunque es posible que los hackers usaran ambos por separado.

