Intezer experts descubierto the TeamTNT cybercriminal group, whose hackers use the legitimate Weave Scope tool in their attacks to visualize and monitor cloud infrastructure. Según los investigadores, this is the first time that attackers have used a legitimate tool for such attacks.
Como se ha mencionado más arriba, Weave Scope is usually used for visualizing and monitoring cloud infrastructure and is often used in conjunction with Docker and Kubernetes, as well as Distributed Cloud Operating System (DC/OS) and AWS Elastic Compute Cloud.
Como resultado, TeamTNT hackers not only visualized the cloud environments of their victims with it, but also executed commands without explicitly deploying malware on the target server.
Analysts remind that the TeamTNT group has been active since at least April of this year and earlier attacked incorrectly configured Docker installations, infectándolos con mineros y bots para ataques DDoS. Luego se supo que los piratas informáticos cambiaron ligeramente sus tácticas.: they began to attack Kubernetes too, and began searching for credentials from Amazon Web Services on the infected servers and steal them. Además, there have now been recorded cases of hackers posting malicious images to Docker Hub.
Actualmente, the tactics of the group’s attacks have not undergone major changes, but the way of gaining control over the infrastructure of the infected host has changed.
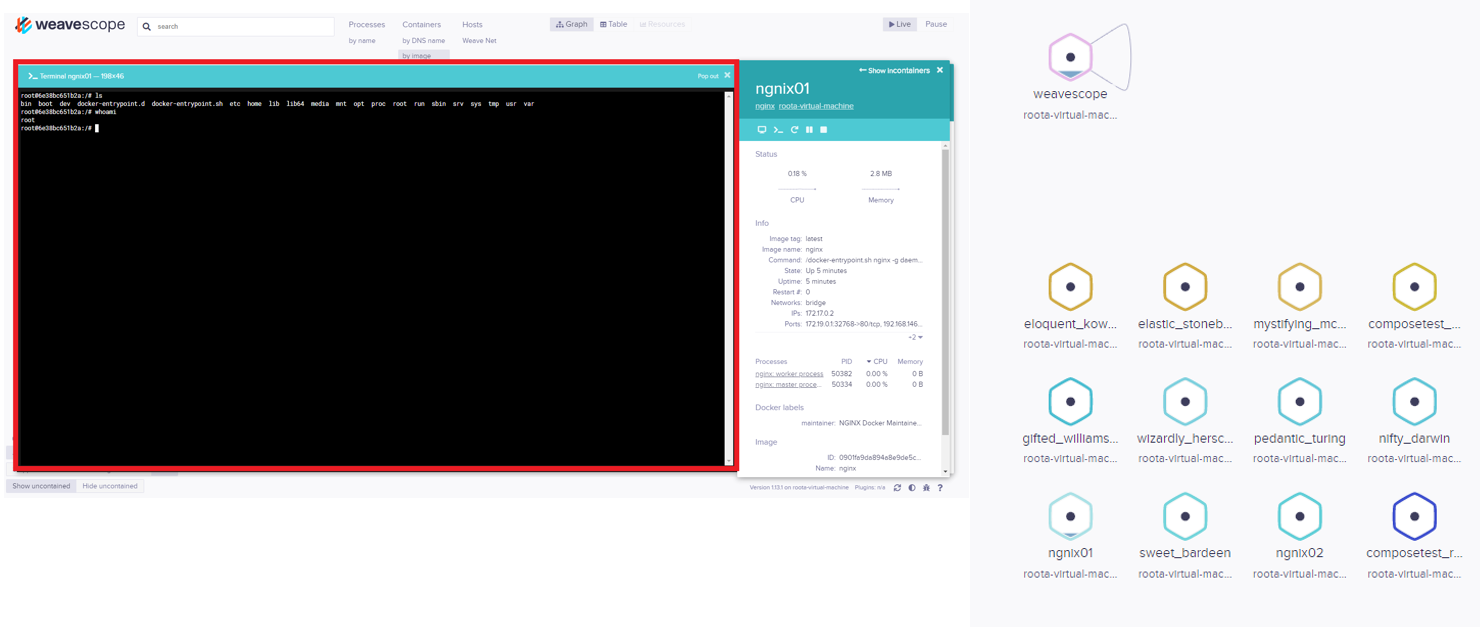
Experts say that after getting inside, hackers create a new privileged container with a clean Ubuntu image, which they use to download and execute miners. Attackers configure the container so that its file system is connected to the file system of the victim server, gaining access to files on the server. The attackers gain root-access, create a local root user hilde to connect to the server via SSH, and eventually install Weave Scope.
“By using a legitimate tool like Weave Scope, attackers get all the benefits of a backdoor installed on the server, but they make much less effort and, en realidad, do not need to use malware”, — write Intezer experts.
The researchers warn that the Weave Scope uses port 4040 by default so that the dashboard is available and anyone with access to the network can view it.
«As well as the Docker API port, this port must be closed or restricted by a firewall», — emphasizes the company.
Déjame recordarte que Google Cloud services are also used for hackers’ attacks.

