Los investigadores de NVISO Labs notaron que el grupo Epic Manchego utiliza archivos Excel inusuales para los ataques., creado específicamente para eludir los mecanismos de defensa. El caso es que estos archivos no se crean a través de Microsoft Office. – los hackers usan la biblioteca .NET EPPlus.
Típicamente, esta biblioteca es utilizada por desarrolladores de aplicaciones, por ejemplo, para agregar funciones como «Exportar a Excel» o «Guardar como hoja de cálculo». La biblioteca se puede utilizar para crear archivos en una amplia variedad de formatos y es compatible con Excel. 2019.
“Parece que los piratas informáticos están utilizando EPPlus para crear hojas de cálculo en Office Open XML (OOXML) formato. A los archivos producidos por Epic Manchego les falta parte del código VBA típico de los documentos Excel compilados en Microsoft Office oficial”, – los expertos escriben.
Resultó que algunos productos antivirus y escáneres de correo electrónico consideran esta parte del código VBA como uno de los posibles signos de un archivo Excel sospechoso., porque, como una regla, este es un almacenamiento para código malicioso . Por lo tanto, Es mucho menos probable que las soluciones de seguridad detecten los archivos especiales de Epic Manchego (en comparación con otros archivos maliciosos de Excel).
Por supuesto, Esto no significa que los archivos de Epic Manchego sean completamente inofensivos.. Aunque los archivos funcionaron correctamente., como cualquier otro documento de Excel, Los expertos explican que los ciberdelincuentes almacenan malware en ellos utilizando un formato de código VBA personalizado., que también está protegido con contraseña para que los sistemas de seguridad y los especialistas en seguridad de la información no puedan analizar el contenido.
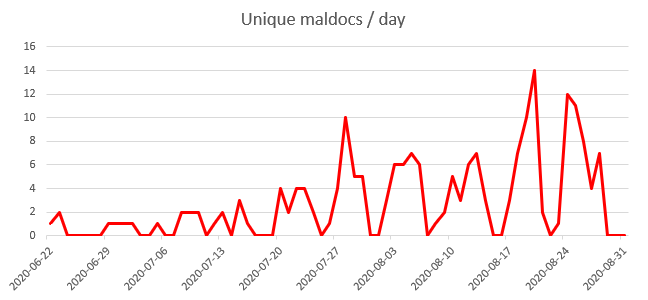
Los analistas señalan que el uso de EPPlus no sólo ayudó, pero también lastimó a Epic Manchego. El hecho es que los expertos pudieron detectar numerosas operaciones de agrupación pasadas simplemente buscando archivos Excel inusuales.. Como resultado, más que 200 Se descubrieron archivos relacionados con Epic Manchego, el primero de los cuales data de junio 22 de este año.
Como puedes adivinar, dichos documentos maliciosos contienen macroscripts de malware. Por ejemplo, si la víctima abre el archivo Excel y permite la ejecución del script, las macros descargarán e instalarán malware en su máquina.
Las cargas útiles en este caso son troyanos clásicos de robo de información como Azorult., AgenteTesla, Libro de formularios, Matiex y njRat, que roban contraseñas de los navegadores, Clientes de correo y FTP y enviarlos a los servidores de Epic Machengo..
Cabe resaltar que, en general, A los expertos de NVISO Labs no les sorprendió que el grupo de hackers estuviera utilizando EPPlus para sus ataques.. ellos escriben:
«Conocemos esta biblioteca .NET desde hace mucho tiempo., ya que lo hemos estado usando durante varios años para crear documentos maliciosos para nuestro equipo rojo y pentesters»
No sólo los usuarios de Excel están bajo ataque, Recientemente escribí que los piratas informáticos utilizan en los ataques. complemento malicioso para 3Ds Max, e incluso Los piratas informáticos obligan a los usuarios a resolver CAPTCHA.