A comienzos de 2020, Los expertos de ESET hablaron sobre la vulnerabilidad Kr00k (CVE-2019-15126), que se puede utilizar para interceptar y descifrar Wi-Fi (WPA2) tráfico. Luego se informó que cualquier dispositivo que utilice las soluciones de Cypress Semiconductor y Broadcom, desde computadoras portátiles y teléfonos inteligentes hasta enrutadores y dispositivos IoT, son susceptibles a este problema. Ahora hay información de que el problema Kr00k amenaza a los dispositivos con chips Wi-Fi Qualcomm y MediaTek.
Así que, en marzo, Expertos de ESET escribió que probaron y confirmaron el problema para iPhone, iPad, Mac, Amazon Echo y Kindle, Nexus de Google, Samsung galaxia, Xiaomi Redmi, Frambuesa Pi 3, así como para enrutadores Wi-Fi de Asus y Huawei. En total, Se pensaba que la vulnerabilidad Kr00k amenazaba a alrededor de mil millones de dispositivos diferentes.
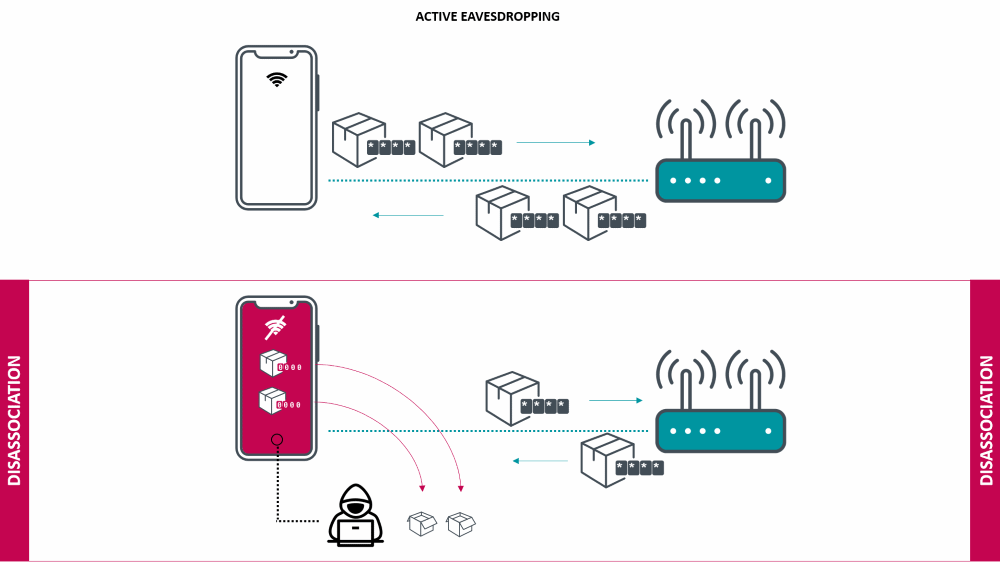
“El problema de Kr00k está asociado con el cifrado, que se utiliza para proteger los paquetes de datos transmitidos a través de Wi-Fi. Típicamente, dichos paquetes están cifrados con una clave única, que depende de la contraseña de Wi-Fi, que estableció al usuario. Sin embargo, para chips vulnerables, esta clave se pone a cero en caso del proceso de disociación, por ejemplo un cierre temporal, que suele ocurrir debido a una mala señal», – dijo a los investigadores de ESET.
De este modo, Los atacantes pueden provocar la transición del dispositivo a un estado de disociación prolongado y recibir paquetes de Wi-Fi destinados a él.. Entonces, explotando el error Kr00k, Los atacantes pueden descifrar el tráfico Wi-Fi utilizando un «cero» llave.
Tras la publicación del informe de febrero de ESET, Los ingenieros de Broadcom y Cypress han publicado correcciones para sus productos.
Sin embargo, Expertos de ESET ahora he advertido que los chips de Qualcomm y MediaTek son vulnerables a fallas similares.
En el caso de Qualcomm, la vulnerabilidad recibió el identificador CVE-2020-3702, y usando este error, un atacante (después de la disociación) puede obtener acceso a datos confidenciales.
«La diferencia con el ataque descrito anteriormente es que los datos capturados en este caso no están cifrados en absoluto., mientras que explotar el problema original de Kr00k al menos requiere el uso de un “cero» llave", – dijeron los expertos.
Los investigadores probaron esta vulnerabilidad utilizando el D-Link DCH-G020 Smart Home Hub y el enrutador inalámbrico Turris Omnia como ejemplos.. Sin embargo, cualquier otro dispositivo que utilice chips Qualcomm vulnerables, También puede verse afectado por el nuevo problema..
Qualcomm lanzó un parche para su controlador propietario en julio 2020, pero la situación se complica por el hecho de que algunos dispositivos vulnerables utilizan controladores de Linux de código abierto, y no está claro si el problema se solucionará allí. Qualcomm dijo que ya ha proporcionado a los OEM todas las instrucciones necesarias., y los usuarios sólo pueden esperar el lanzamiento de parches de fabricantes específicos.
Además, Los expertos de ESET descubrieron que los chips MediaTek, que son ampliamente utilizados en los enrutadores Asus, así como en el kit de desarrollo Microsoft Azure Sphere, Tampoco utilice cifrado en absoluto.
«Azure Sphere utiliza el microcontrolador MediaTek MT3620 y se dirige a una amplia variedad de aplicaciones de IoT, incluyendo hogares inteligentes, comercial, industria y muchos otros sectores», — escriben los investigadores.
MediaTek publicó correcciones para este problema en marzo y abril, y Azure Sphere recibieron parches en julio 2020.
En medio del lanzamiento de una serie de exploits para la vulnerabilidad Kr00k original, los investigadores han publicado un guión especial que ayudará a descubrir si el dispositivo es vulnerable al Kr00k original o a nuevas variaciones de este ataque.

