Con el número cada vez mayor de amenazas cibernéticas, Los piratas informáticos y los especialistas en ciberseguridad están tomando la iniciativa.. Esta vez, Los ciberdelincuentes se adelantaron a la curva.. ellos crearon un sitio web de phishing para coincidir con la noticia que Microsoft estaba desarrollando una billetera criptográfica exclusivamente para su navegador Edge. Este esquema se utiliza para difundir a Luca Stealer.
La estafa de Microsoft Crypto Wallet propaga a Luca Stealer
No hace tanto tiempo, la noticia saltó en internet eso Microsoft está trabajando en la creación de una billetera criptográfica para su navegador Edge. Esta noticia seguramente interesará a los usuarios de criptomonedas. Pero ya sabes a quién más le interesa.? Así es, ciberdelincuentes. Los ingeniosos muchachos se dieron cuenta inmediatamente de lo que estaba pasando y creó un sitio web que se parecía lo más posible al sitio legítimo de Microsoft. Investigadores de ciberseguridad encontraron este sitio web y lo analizaron.. A diferencia de los sitios de phishing de tercera categoría, éste tenía una apariencia convincente, una dirección web de hxxps[:]//microsoft-en[.]es/cryptowallet/, Certificados SSL, y la lógica conocida. El sitio web ofrece al usuario descargar una versión beta de la billetera criptográfica.. Sin embargo, en lugar del reclamado, el usuario malware recibido.
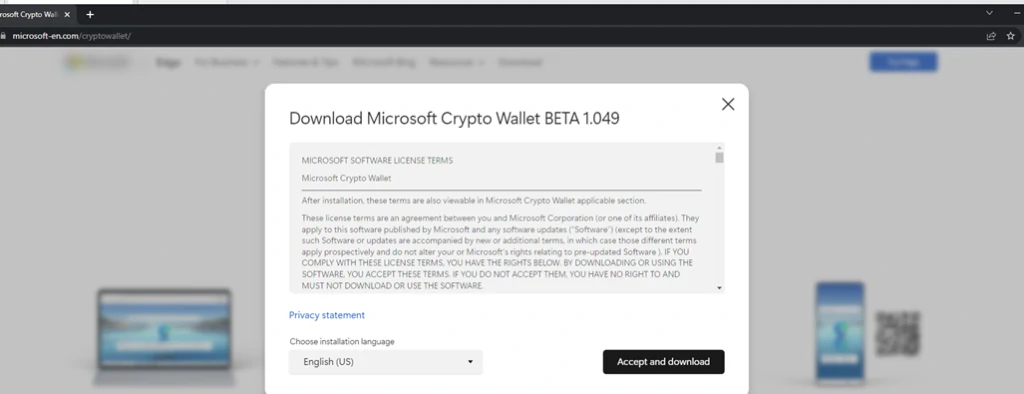
Análisis del ladrón de Luca
En este caso, los estafadores son distributing Luca Stealer. Los especialistas lo identificaron por similitudes entre el código malicioso encontrado y el Luca Stealer.. Sin embargo, Luca es de código abierto, que los usuarios pueden encontrar en plataformas como GitHub o TOR. Es un ladrón relativamente nuevo., escrito en Rust y visto por primera vez en 2022. Su trabajo es para recopilar datos valiosos, como detalles de la billetera criptográfica y otra información personal. Los siguientes son los navegadores., billeteras criptográficas, y extensiones que ataca este malware.
Navegadores web
| CentBrowser | Iridio | surfear | Canario cromado |
| Resbaladizo 5 | vivaldi | Explorador de elementos | Navegador CocCoc |
| Antorcha | Establo de ópera | Corajudo | Cometa |
| Borde | CocMedia | Google Chrome | Estudio de arce |
| CozMedia | ChromePlus | Átomo | Cromo |
| navegador de la UC | Opera GX | WooGamble | Ópera |
| Dragón (Dragón conveniente) | Cromo SxS | 7estrella | Sputnik |
| Navegador de privacidad épico | Chedot | Carrera | citrio |
| órbita | Cromo |
Extensiones del navegador
| 1Contraseña | Administrador de contraseñas de Avira | Monedero BitApp | Bitclip |
| bitwarden | Cadena Binance | NavegadorPass | Por uno |
| Cartera Trébol | moneda98 | Monedero Coinbase | Clave común |
| Cartera ciano | Monedero ciano Pro | DAppPlay | Dashlane |
| Autenticador EOS | Cartera IGUAL | Guardia | Cliente Hycon Lite |
| iconoex | KHC | KeePassXC | Guardián |
| Keplr | Ultimo pase | Cartera de hoja | Cartera de calidad |
| Cartera de Matemáticas | MEW CX | MetaMáscara | miki |
| Cartera Nabox | Extensión Nash | NeoLine | NordPass |
| Cartera ingeniosa | Administrador de contraseñas de Norton | Una llave | Cartera de polimalla |
| RoboForm | sollet | división | Llavero de vapor |
| TezBox | Estación Terra | TronLink | Administrador de contraseñas de Trezor |
| wombat | Yoroi | ZilPay | Bóveda de Zoho |
Carteras criptográficas
- Cartera Atómica
- ByteCoin
- electro
- éxodo
- JaxxWallet
Además de las criptomonedas, el malware está interesado en datos bancarios como IBAN. Esto crea riesgos adicionales para quienes participan en transacciones bancarias..
Exfiltración de datos
Una vez recopilados los datos, Luca Stealer comienza a comprimir los datos para facilitar la transmisión. El malware utiliza la plataforma de mensajería Telegram como canal de comunicación encubierto. Usando un bot de Telegram, envía discretamente datos robados y cierta información estadística sobre los datos robados al operador. También envía mensajes a la sala de chat..
¿Por qué Luca Stealer??
Desde que se filtró al público el código fuente de Luca Stealer, los atacantes pueden modificarlo, optimizarlo y agregar nuevas funcionalidades. Después de un análisis más detallado, Los expertos descubrieron un método AntiVM inusual. Luca Stealer comprueba la temperatura del sistema antes de comenzar a ejecutar. Dado que las máquinas virtuales suelen generar un error cuando se realiza dicha solicitud, el malware puede entender si está en la máquina virtual o en un sistema en vivo. Aunque, este truco consiste simplemente en hacer que el análisis sea más largo en lugar de imposible. No es difícil hacer que la VM responda adecuadamente a la solicitud., devolver temperaturas realistas y consistentes.
Recomendaciones de seguridad
Para evitar consecuencias desagradables., te recomendamos seguir los siguientes consejos:
- Cuidado con las descargas de Internet. Descargue software sólo de fuentes oficiales y confiables. Si tienes dudas sobre la autenticidad de un sitio web, Vaya a un sitio web confiable y asegúrese de que el sitio que le interesa sea genuino..
- Actualiza tu software. A veces las actualizaciones del sistema operativo pueden ser un inconveniente. Sin embargo, Esta es una parte esencial ya que las actualizaciones contienen parches de seguridad.. Para abordar vulnerabilidades conocidas, actualice constantemente su sistema operativo y otro software, incluyendo navegadores.
- Cuidado con los mensajes de correo electrónico. According to statistics, El phishing por correo electrónico es uno de los métodos más eficaces para propagar malware.. No abra archivos adjuntos ni enlaces sospechosos en correos electrónicos de remitentes desconocidos.
- Instale un software antivirus confiable. Usar software antimalware de calidad y actualícelo periódicamente para mantenerse protegido de las últimas amenazas.
- Infórmese y manténgase informado. Desgraciadamente, en esta eterna carrera armamentista, los ciberdelincuentes están liderando. Esto les permite crear nuevas amenazas., elegir las formas menos predecibles cada vez. Sucesivamente, Expertos en ciberseguridad crean soluciones efectivas contra ellos. Estudia amenazas y técnicas de engaño actualizadas para ser más consciente y adaptar tus acciones.


