Expertos en BitDefender found Mandrake spyware in the official Android app store, hiding on Google Play for four years (desde 2016).
The malware established full control over infected devices, collected credentials, GPS from infected devices, made screen recordings, etcétera.
Al mismo tiempo, the malware carefully avoided infections in countries such as Ukraine, Bielorrusia, Kyrgyzstan and Uzbekistan, Africa and the Middle East.
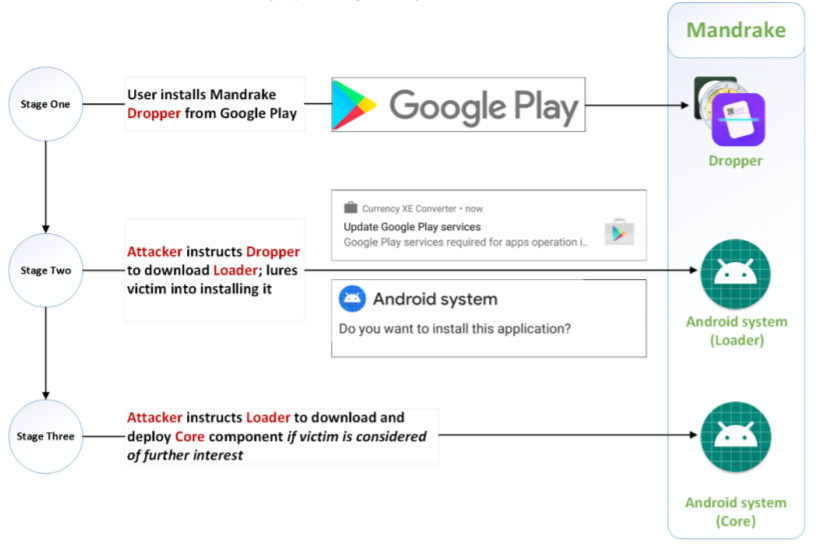
Mandrake has a three-stage structure, which allowed its operators to avoid detection by Google Play security mechanisms for a long time. It all started with a harmless dropper placed in the official application catalog and disguised as a legitimate application, such as a horoscope or cryptocurrency converter.
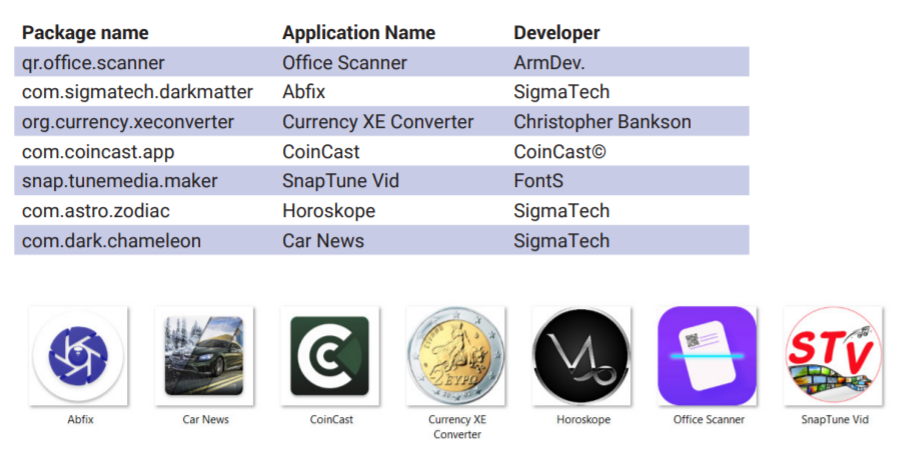
When such an application was downloaded on the victim’s device, the dropper downloaded the bootloader from the remote server. Al mismo tiempo, the dropper himself was able to remotely turn on Wi-Fi, collect information about the device, hide its presence about the victim and automatically install new applications.
Sucesivamente, the bootloader was already responsible for direct downloading and installing Mandrake malware.
“The malware completely compromised the target device, gave itself administrator privileges (the request for rights was masked as a license agreement), after which it gained wide opportunities: forwarding all incoming SMS messages to the attackers’ servidor; sending messages; making calls; stealing information from the contact list; activating and tracking of the user’s location via GPS; stealing Facebook credentials and financial information and screen recording”, – report Bitdefender specialists.
Además, the malware carried out phishing attacks on Coinbase, Amazonas, Gmail, Google Chrome, applications of various banks in Australia and Germany, the currency conversion service XE and PayPal.
Peor, Mandrake is able to reset the infected device to the factory settings in order to erase user data, as well as all traces of the malware’s activity. When the attackers received from the victim all the information they needed, Mandrake went into the «destruction mode» and erased himself from the device.
“We believe that the number of victims of Mandrake is tens or even hundreds of thousands, but we don’t know the exact number”, — writes Bitdefender expert Bogdan Botezatu.
The company’s researchers believe that for four years, all spyware attacks were coordinated by its operators manually and were not fully automated, as is usually the case. They also note that Mandrake was not spread by spam, and it seems that the attackers carefully selected all their victims.
Specialists were able to trace the Mandrake developer account on Google Play to a certain Russian-speaking freelancer hiding behind a network of fake company websites, stolen IDs and email addresses, as well as fake job ads in North America.
As for Friday, I remind you that For eight years, La botnet Cereals existía con un solo propósito.: descargo anime.

