Microsoft analysts have prepared a traditional Digital Defense report, in which they talked about the main events and trends in the field of cybersecurity and threat analysis over the past year (from July 2019 a junio 2020). La empresa, por ejemplo, estimated that some ransomware attacks could be carried out in less than 45 acta.
Los expertos escriben que, en primer lugar, everyone will remember 2020 due to the coronavirus pandemic. While some hacker groups have used the COVID-19 theme in their attacks, Microsoft says these operations were only a small part of the overall malware ecosystem, and the pandemic appears to have played a minimal role in the attacks of the past year.
“The number of phishing attacks on the corporate sector continues to grow and are becoming the dominant vector. Most phishing lures are centered around Microsoft and other SaaS vendors, and the top five fraudulent brands include Microsoft, UPS, Amazonas, Apple and Zoom”, – write Microsoft analysts.
En total, Microsoft blocked more than 13,000,000,000 malicious and suspicious emails in 2019, more than a billion of which contained phishing URLs.
Además, successful phishing operations are often the first step in BEC attacks. Eso es, fraudsters gain access to the mailbox of a company executive, examine his email, and then trick the compromised user’s business partners into paying bills and sending funds to their bank accounts. The report states that BEC scammers are most often interested in credentials from the C-suite accounting product.
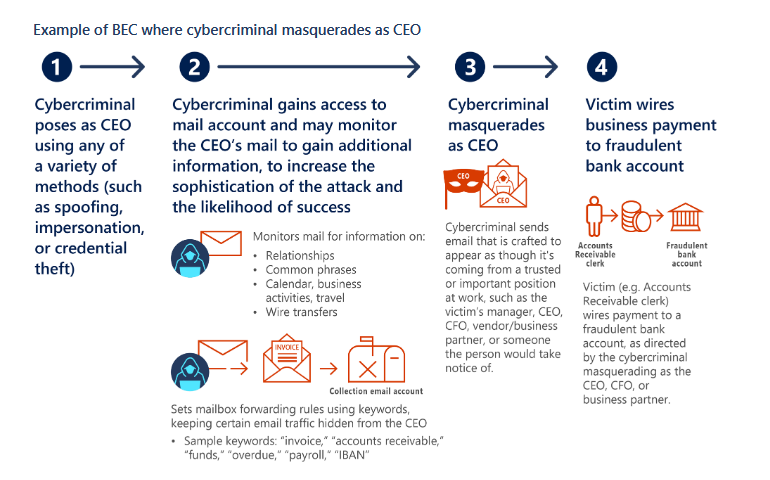
Sin embargo, phishing isn’t the only way to break into someone else’s account.
También, hackers use the password spraying technique and often exploit the fact that users reuse the same passwords. In the mentioned technique, attackers go through different usernames and try to use them with the same simple, contraseña fácil de adivinar, in the hope of finding a poorly secured account.
“These attacks are most often used against IMAP and SMTP. They allow attackers to bypass multi-factor authentication because login via IMAP and SMTP does not support this feature”, – say Microsoft researchers.
Microsoft experts unambiguously call ransomware the most serious threat over the past year.
Most of this activity came from hack groups that specialize in attacks on large corporations or government organizations, since they can get the most significant ransom. Most of these groups either exploit infrastructure provided by other hackers or massively scan the Internet for recently discovered vulnerabilities.
En la mayoría de los casos, hackers infiltrate the system and stay there, waiting until they are ready to launch an attack.
Microsoft reports that ransomware has been particularly active this year and has dramatically reduced the time it takes to launch attacks, especially during the COVID-19 pandemic.
“Attackers used the COVID-19 crisis to reduce the time spent on the victim’s system. They compromise, robar datos, y, en algunos casos, quickly activate ransomware, apparently in the belief that they would be more likely to get paid that way. En algunos casos, cybercriminals went from initial infiltration to encrypting the entire network and demanding a ransom in less than 45 minutes”, — said the report.
Let me remind you that the researchers also calculated that Los ataques de ransomware ocurren con mayor frecuencia por la noche y los fines de semana..

