Seguridad móvil
Microsoft warns of dangerous vulnerability in Surface Pro 3 devices
Los ingenieros de Microsoft han publicado un boletín de seguridad sobre una nueva vulnerabilidad que afecta a Surface Pro 3 tabletas. The bug could be…
Ukrainian cyber police arrested ransomware operators who «earned» $150 million
La policía cibernética de Ucrania arrestó a dos operadores de un ransomware anónimo. It is reported that the operation was carried out…
Experts showed fraudulent payments from a locked iPhone with Apple Pay and a Visa card
Scientists talked about how to make fraudulent payments using Apple Pay with a Visa card on a locked iPhone. Éste…
Encryption algorithms for 2G networks have been intentionally weakened
A group of scientists from several European universities published a report on encryption algorithms for 2G networks, which many information…
Google stopped trying to shorten URLs in the address bar
El experimento de Google con el intento de acortar las URL (ocultar partes de la URL de la barra de direcciones) has finally failed and…
Microsoft urges users to opt out of multi-factor authentication via phone
Los expertos de Microsoft han vuelto a plantear la cuestión de la…
Platypus attack allows stealing data from Intel processors
Un grupo de científicos de la Universidad Técnica de Graz…
Experts discovered that many mobile browsers are vulnerable to url spoofing
Rapid7 analysts and independent information security expert Rafay Baloch discovered…
MalLocker ransomware easily tricks Russians, pretending to be a screen lock from the police
Microsoft experts talked about the new Android ransomware AndroidOS/MalLocker. (hereinafter…
Cellmate men’s chastity belts are vulnerable to attacks and dangerous for users
Pen Test Partners analysts have studied an extremely unusual device:…
Google recruits a team of experts to find bugs in Android applications
ZDNet reports that a number of new positions have been…
Attackers can bypass TikTok multi-factor authentication through the site
Journalists of the ZDNet publication, citing one of their readers,…
Microsoft left open one of the internal servers of the search engine Bing
Ata Hakcil, especialista en ciberseguridad en WizCase, discovered that Microsoft…
SpiKey technique allows opening the lock by recording a sound of a turning key
Scientists from the National University of Singapore have published a…
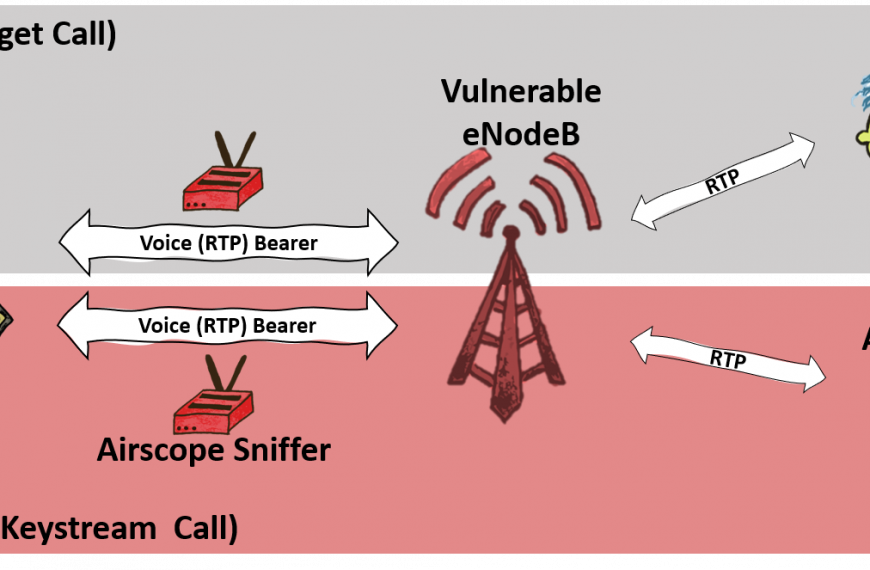
ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Experts from the Ruhr University and New York University in…
Citrix expects attacks on fresh issues in XenMobile
Los ingenieros de Citrix lanzaron varios parches de Citrix Endpoint Management…
Media Reports that Garmin Paid Ransom to WastedLocker Malware Operators
En julio 2020, garmin, el fabricante de electrónica portátil y…