Investigadores de seguridad de la información en ReversingLabs reportado el descubrimiento de 725 Bibliotecas maliciosas que robaron el contenido del portapapeles en el repositorio oficial de Rubygems.
RUbygems es un administrador de paquetes para el lenguaje de programación de Ruby. Según sus propias estadísticas de sitio, El repositorio contiene alrededor 158 mil paquetes (Llamadas gemas) con casi 49 mil millones de descargas totales.
Se puede ver una lista completa de bibliotecas aquí.
Los paquetes maliciosos se subieron a Rubygems desde febrero 16 a febrero 25, 2020 De dos cuentas: Jimcarrey y Petergibbons.
Los investigadores escriben que el malware fue eliminado de Rubygems ya en febrero 27, Dos días después de que ReversingLabs notificó a los desarrolladores de su hallazgo.
Todos los malware detectado eran clones de varias bibliotecas legítimas. Usaron la técnica de typosquatting., Eso significa que tenían nombres deliberadamente similares a los originales, e incluso funcionó como se esperaba, pero también contenía archivos maliciosos adicionales.
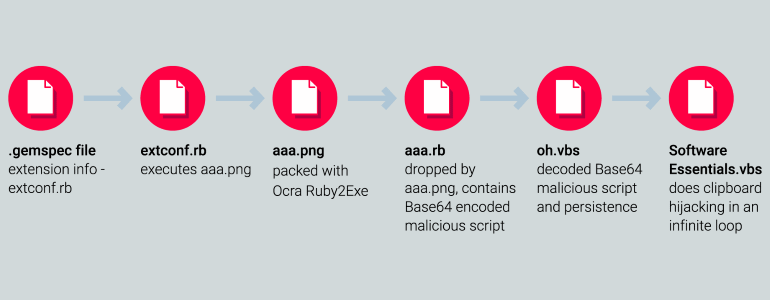
Un archivo adicional integrado en cada paquete se llamaba aaa.png. A pesar de la extensión, Este archivo no era una imagen PNG. De hecho, Era un ejecutable de Windows PE.
A propósito, Ya he escrito sobre cómo los cibercriminales encrypt malware en las imágenes: por ejemplo, MyKingz botnet uses Taylor Swift photo to infect target machines.
La instalación de cualquiera de las bibliotecas maliciosas causó una cadena de las siguientes acciones:
- El archivo PE creó un script de Ruby llamado AAA.RB que contiene el intérprete Ruby y todas las dependencias necesarias para ejecutar;
- Este script creó un script de Visual Basic llamado Oh.vbs;
- El script creó una clave para Autorun en el registro;
- La tecla de inicio ejecutó el segundo script Visual Basic cada vez que la computadora comenzó o reinició;
- El segundo script interceptó los datos enviados al portapapeles, y busqué plantillas similares a las direcciones de las billeteras de criptomonedas, y los reemplazó con la billetera de un atacante.
ReversingLabs escribe que miles de usuarios luego han descargado estas bibliotecas. Sin embargo, A juzgar por la dirección de bitcoin del atacante, Durante todo el tiempo de la actividad de la campaña, no pudo interceptar ningún pago, Cambiar la dirección a la suya.
Los investigadores creen que detrás de este ataque hay la misma persona o grupo que cargó bibliotecas maliciosas en Rubygems antes, en 2018 y 2019. Ambos incidentes se distinguieron mediante el uso de métodos similares, y el objetivo era robar la criptomoneda de los usuarios.

