Desarrolladores de GitHub han emitido una advertencia sobre la aparición del nuevo malware Octopus Scanner, que se distribuye en el sitio a través de proyectos Java maliciosos.
Octopus Scanner fue descubierto en proyectos gestionados con el IDE de Apache NetBeans, una herramienta utilizada para escribir y compilar aplicaciones Java.
Después de un aviso recibido en marzo de investigadores de seguridad de la información, los desarrolladores encontraron 26 repositorios que contienen malware. La lista de repositorios para la advertencia., desafortunadamente, no está adjunto.
“Cuando los usuarios descargaron cualquiera de estos 26 proyectos, el malware se comportó como un gusano que se propagaba a sí mismo y continuó infectando las computadoras locales. Octopus Scanner escaneó la estación de trabajo en busca de una instalación local de NetBeans IDE y la implementó en otros proyectos Java víctimas”., – explicar a los representantes de GitHub.
El malware fue adaptado para funcionar con Windows, macOS y Linux, y finalmente descargó el troyano de acceso remoto (RATA), permitiendo a sus operadores profundizar en los archivos de la computadora de la víctima en busca de información confidencial.
GitHub informa que la campaña Octopus Scanner duró varios años. La muestra más antigua de malware se subió a VirusTotal en agosto 2018. aunque solo 26 Se encontraron repositorios con rastros de Octopus Scanner en GitHub, Los expertos creen que en los últimos dos años., muchos más proyectos han sido infectados.
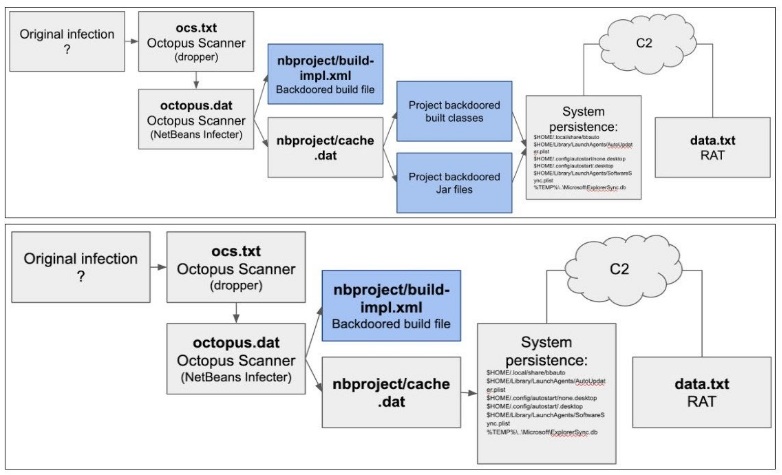
Aparentemente, El verdadero propósito de estos ataques era colocar el RAT en las máquinas de personas que trabajan en proyectos importantes o en grandes empresas que desarrollan software.. Esto permitió a los atacantes robar información confidencial sobre los próximos lanzamientos., código fuente propietario e incluso puertas traseras, incrustar en software corporativo u otro software de código cerrado.
“Curiosamente, este programa malicioso atacó específicamente a NetBeans, porque hoy en día no es el IDE de Java más común. Si los creadores del malware dedicaron tiempo a implementar este malware específicamente en NetBeans, esto podría significar que fue un ataque dirigido, o probablemente ya tenían implementaciones de malware para sistemas de compilación como Make, msconstruir, Gradle, etcétera, y podría pasar desapercibido”, — escriben expertos de GitHub.
Permítanme recordarles que recientemente el servicio web de representantes de GitHub advirtió a los usuarios sobre un ataque masivo de phishing llamado pez sierra.

