Noticias, Consejos, Laboratorio de seguridad
Hackers Broke into Activision’s Slack and Stole Data
Activisión, el editor de juegos de computadora (incluyendo la franquicia Call of Duty), informó de una violación de seguridad que ocurrió en…
Five Easy Smartphone Security Tips to Keep It Safe From Hackers
Estos días, El teléfono inteligente es más que un simple medio de comunicación.. Todos los días lo usamos para comunicarnos con…
How DDoS Can Badly Hurt Your Business
Todo el mundo se ha enfrentado al menos una vez al hecho de que no puede ir al sitio deseado ni utilizar algún servicio.. Éste…
Cybersecurity Experts Discovered a New Stealc Infostealer
Los expertos de ekoia informan que un nuevo ladrón de información, Huelga, ha aparecido en la red oscura, and is gaining popularity among criminals due…
Hackers Attacked GoDaddy and Stayed on the Company’s Systems for Several Years
Uno de los proveedores de alojamiento y registradores de nombres de dominio más grandes del mundo., Ve papi, informa que los piratas informáticos han comprometido la infraestructura de la empresa. Peor,…
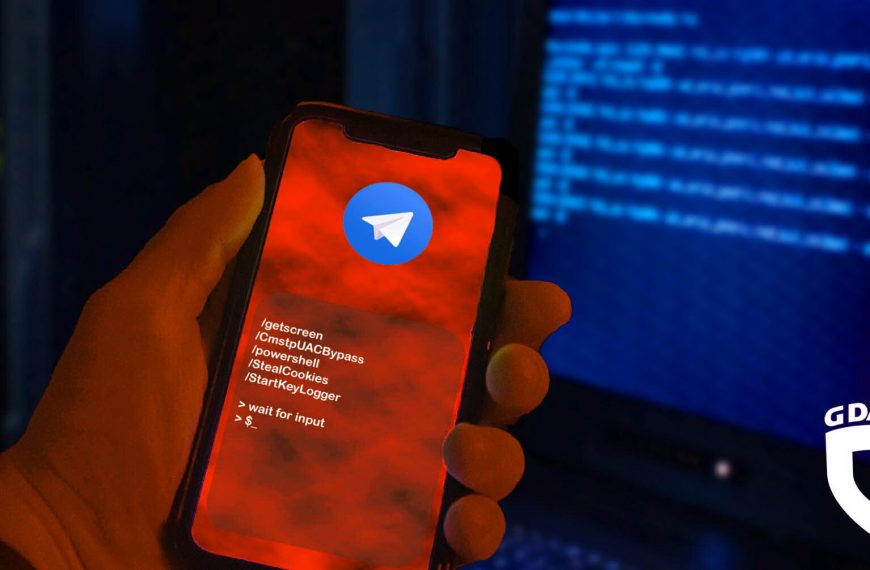
New T-RAT malware can be controlled via Telegram
G DATA’s specialists have published a report on the new…
Experts discovered that many mobile browsers are vulnerable to url spoofing
Rapid7 analysts and independent information security expert Rafay Baloch discovered…
Google engineers fixed Chrome 0-day vulnerability that was already under attacks
Los ingenieros de Google han lanzado una versión actualizada de Google Chrome…
Bughunter stole a Monero exploit from another cybersecurity specialist and received a reward for it
Bleeping Computer reporters drew attention to an interesting case that…
P2P botnet Interplanetary Storm accounts more than 9000 devices
Bitdefender experts gave a detailed description of the work of…
Google revealed the most powerful DDoS attack in history
Esta semana, the Google Cloud team talked about a previously…
Google and Intel experts warn of dangerous Bluetooth bugs in Linux
Google and Intel engineers warn of dangerous Bluetooth bugs that…
Hackers are increasingly using open source tools for attacks
Hablando en la conferencia Virus Bulletin, Intezer Labs analysts said…
Attackers can use Windows Update client to execute malicious code
Hackers can exploit Windows Update client to execute malicious code…
Five Eyes Alliance, India and Japan Call for Backdoors in Software
Países que participan en la Alianza Cinco Ojos (which brings together…
MalLocker ransomware easily tricks Russians, pretending to be a screen lock from the police
Microsoft experts talked about the new Android ransomware AndroidOS/MalLocker. (hereinafter…
Cellmate men’s chastity belts are vulnerable to attacks and dangerous for users
Pen Test Partners analysts have studied an extremely unusual device:…