Noticias, Consejos, Laboratorio de seguridad
Cryptocurrency Scam “Pig Butchering” Penetrated the Apple App Store and Google Play Store
La estafa de la matanza de cerdos, una operación fraudulenta que se especializa en inversiones falsas en proyectos de criptomonedas supuestamente prometedores, cepo, cautiverio, futuros…
Vulnerability in KeePass Allows Stealing All User Passwords in Plain Text
The developers of the open-source password manager KeePass explain that a vulnerability that allows an attacker to steal all user…
Change in the IP Address of the Router Caused a Massive Outage of Microsoft Services
La semana pasada, Microsoft 365 Los servicios en todo el mundo sufrieron una importante interrupción que duró unas cinco horas.. como la empresa…
Microsoft Will Block Excel XLL Files Downloaded from the Internet
Los desarrolladores de Microsoft van a bloquear algún complemento de Excel (.44) archivos para Microsoft 365. The new measures will include automatic…
Ransomware Revenues Dropped by 40% because Victims Refuse to pay
Ingresos por ransomware (de ataques de ransomware) ha caído de $765.6 millones en 2021 a $456.8 millones en 2022, según Chainalysis…
Ukraine’s largest IT company SoftServe has been attacked by a ransomware
Una de las empresas de TI más grandes de Ucrania., Servicio débil (número…
KryptoCibule malware steals cryptocurrency from Windows users
ESET specialists discovered the KryptoCibule malware, which has been active…
Shlayer malware bypassed Apple security checks
Security expert Peter Dantini discovered that the Shlayer malware bypassed…
Scientists have developed an attack that allows not to enter a PIN code while paying with Visa cards
Scientists from the Swiss Higher Technical School of Zurich have…
Elon Musk confirmed that the Russian offered a Tesla employee a million dollars for hacking the company
A principios de esta semana, the US Department of Justice announced the…
Twitter and Graphika neutralized Dracula propaganda botnet
Experts from the Graphika research group talked about how they…
Hackers use in attacks malicious plugin for 3Ds Max
Bitdefender experts have discovered a hacker group that is attacking…
SpiKey technique allows opening the lock by recording a sound of a turning key
Scientists from the National University of Singapore have published a…
Ukrainian cyber police in cooperation with Binance detained operators of 20 cryptocurrency exchangers
Desde enero 2020, the Ukrainian cyber police began cooperating with…
Microsoft developers will stop supporting classic Edge and IE 11
Microsoft dijo que dejaría de admitir Edge e IE clásicos…
Vulnerabilities in Amazon Alexa opened access to user data for outsiders
In June this year, researchers from Check Point discovered a…
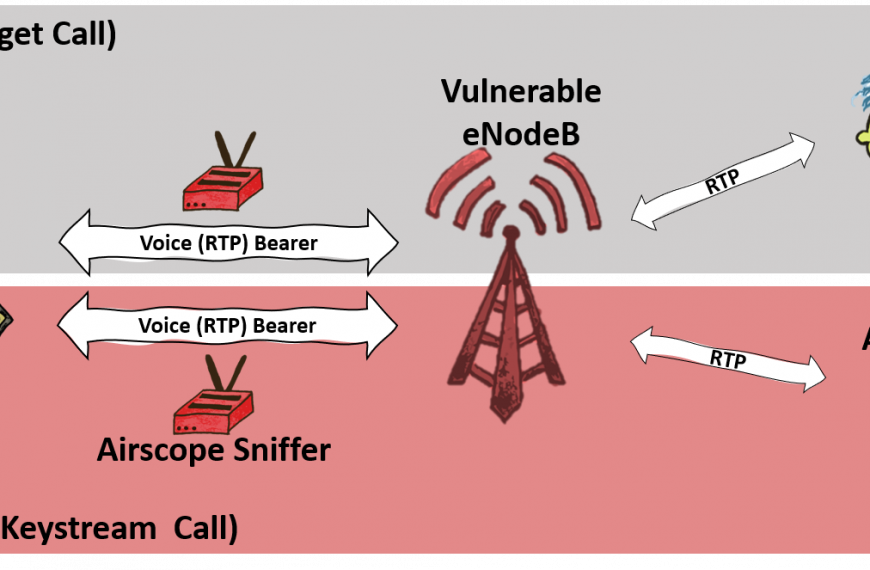
ReVoLTE attack allows overhearing other people’s conversations in LTE networks
Experts from the Ruhr University and New York University in…