Noticias, Consejos, Laboratorio de seguridad
Luca Stealer Spreads Via a Phishing Microsoft Crypto Wallet Site
Con el número cada vez mayor de amenazas cibernéticas, Los piratas informáticos y los especialistas en ciberseguridad están tomando la iniciativa.. Esta vez, cybercriminals went ahead…
Trojan HotRat Is Distributed through Pirated Versions of Software and Games
Los expertos de Avast han advertido que una nueva variante del malware AsyncRAT, llamado HotRat, is distributed through pirated versions of popular…
Gozi and IcedID Trojans Spread via Malvertising
La publicidad maliciosa en la Búsqueda de Google es un fenómeno desagradable en el que aparecen anuncios maliciosos en los resultados de los motores de búsqueda.. These ads are meant…
Vulnerability in WordPress Plugin WooCommerce Payments Is Actively Used to Hack Sites
Los piratas informáticos utilizan una vulnerabilidad en el complemento de WordPress WooCommerce Payments, ampliamente utilizado, para obtener privilegios de cualquier usuario., incluido el administrador,…
Fake Ads on Facebook Promote Scam AI Services
Facebook se ha visto afectado por una ola de anuncios falsos que ofrecen lo que parecen servicios de inteligencia artificial.. De hecho, aquellos…
Dangerous Injection Attacks
Hoy, Injection attacks are a significant problem and top the…
Chinese Hacker Group Revealed after a Decade of Undetected Espionage
The New Chinese Spying Threat Actor Identified SentinelLabs, an American…
Information Security Experts Told About The Linux Malware Symbiote That Is Almost Undetectable
BlackBerry and Intezer specialists spoke about the new Symbiote Linux…
Joint Operation: SSNDOB Personal Data Darknet Market Seized
What SSNDOB Was Before Its Servers Were Seized The US…
Beware: New SpaceX Bitcoin Giveaway Scam
Crooks Make Elon Musk a Bait for Wannabe Cryptotraders Scammers…
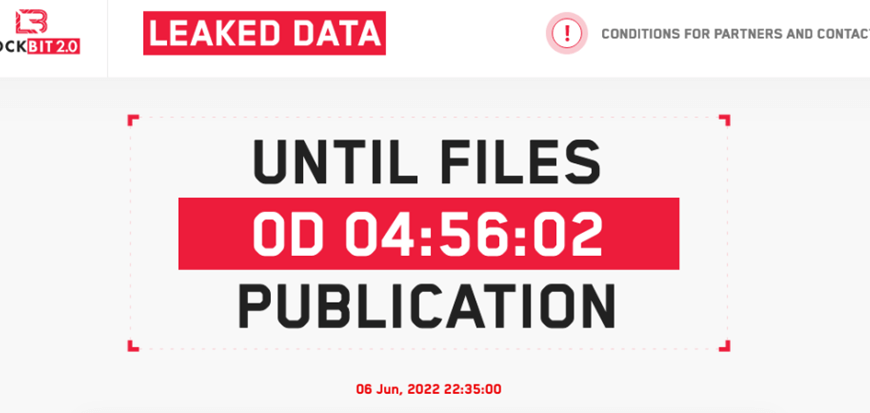
LockBit 2.0 Promises to Leak Mandiant Data
BloquearBit 2.0 anuncio: cosa real o trolling vengativo? En Junio…
Microsoft Is in No Hurry to Fix the Follina Vulnerability, Which Has Become a Real Disaster
Los piratas informáticos están explotando activamente la vulnerabilidad crítica de día 0 de Follina, cual…
Top Types of Spoofing Attacks
suplantación de identidad 1 Spoofing it is an internet scam technique that…
Facts to Remember About Trojan Malware
En este artículo, consideraremos uno de los más viles,…
Attackers Exploit MSDT Follina Bug to Drop RAT
Security specialists caution users about the exploitation of the recently…
New Cuba Ransomware Variant Involves Double-Extortion Scheme
What’s new in April Variant of Cuba Ransomware The Cuba…
The Heuristic Virus & Analysis: Everything You Need To Know
This article targets individuals who have received a computer notification…