Noticias, Consejos, Laboratorio de seguridad
FIN8 Updated Sardonic Backdoor to Deliver Noberus Ransomware
FIN8, un infame grupo de ciberdelincuentes, ha actualizado su malware de puerta trasera para evitar ser detectado. They made improvements and prepared…
Citrix and Adobe Vulnerabilities Under Active Exploitation
Citrix pudo parchear una vulnerabilidad de día cero, while Adobe warns of attacks using ColdFusion Zero-Day and releases an urgent…
Trojanized TeamViewer Installer Spreads njRAT
Según los informes, los actores de amenazas comenzaron a utilizar TeamViewer falso para distribuir malware. Their particular favourite for the final payload is the infamous…
Hundreds of Military and Intelligence Agencies Uploaded Data to VirusTotal
Un empleado de la plataforma VirusTotal, propiedad de Google, subió accidentalmente un archivo con los nombres, email addresses and other data of…
Meduza Stealer: What Is It & How Does It Work?
El mundo del Malware evoluciona constantemente, y sería imprudente ignorar a los recién llegados y su potencial. Meduza Stealer appears to…
Evil Corp Switched to Using LockBit Malware to Avoid Sanctions
The Evil Corp group switched to using the LockBit ransomware…
Warning Signs Of DDoS Attack: Symptoms
DDoS attacks can sometimes have devastating effects on various internet…
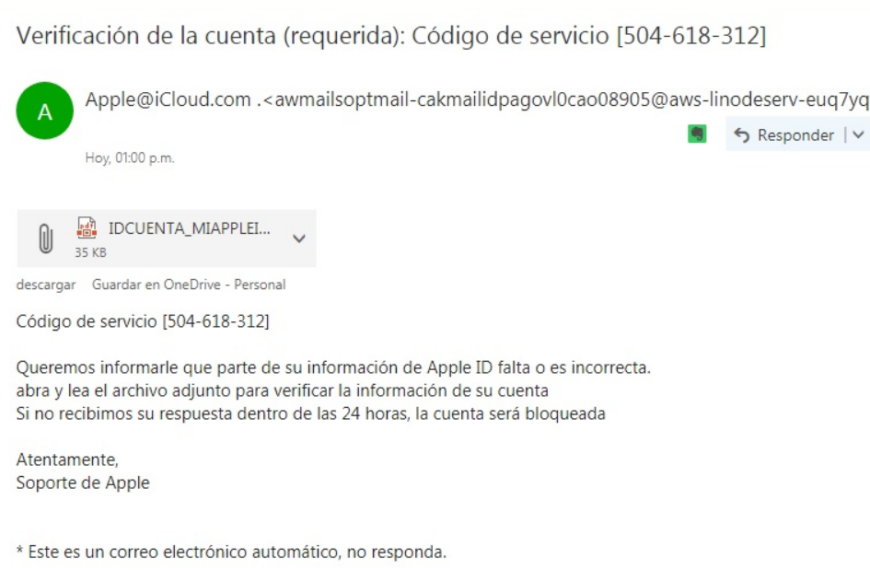
Extension spoofing strikes Spanish-speaking countries
An old-good form of malware disguisment sparked recently in several…
Types of SQL Injection: Attack Examples
Como escribimos en uno de los artículos., SQL is…
Malware VS Ransomware: What’s the Difference?
To deal with any problem successfully you should first have…
TOP 7 Types of Password Attacks
¿Qué es un ataque de contraseña?? Al principio, you probably…
Critical Vulnerability in UNISOC Devices Patched
UNISOC-chip Android Phones are Vulnerable to Remote Modem-Targeting Attacks In…
Information Security Specialists Discovered a 0-day Vulnerability in Windows Search
A new 0-day Windows Search vulnerability could be used to…
Clipminer – a Million Dollar Clipboard Hijacking Coinminer
Clipminer Malware A bizarrely efficient botnet cryptocurrency miner has been…
CMD-Based Ransomware YourCyanide With Info-Stealing Functions
Nueva amenaza: YourCyanide Ransomware CMD-based ransomware YourCyanide, actualmente en desarrollo,…
Most Common Cyber Attacks Today: Tips for Protection
Cyber attacks technologies have become more sophisticated and sophisticated in…
Difference Between Phishing and Spoofing
¿Qué es un ataque de phishing?? Phishing is a cyber-attack method…