Noticias, Consejos, Laboratorio de seguridad
Microsoft CVE-2023-36884 Vulnerability Exploited in the Wild
En julio 11, 2023, Microsoft publicó un artículo sobre cómo abordar la vulnerabilidad CVE-2023-36884. This breach allowed for remote code execution…
Researchers Found BlackLotus UEFI Bootkit Sources on GitHub
El código fuente del kit de arranque UEFI BlackLotus, que anteriormente se vendía en la web oscura por $5,000, ha sido…
What is Cyber Risk Exposure and How Can You Manage It?
Las empresas modernas se enfrentan diariamente a amenazas de ciberseguridad. Si bien la mayoría son efectivamente neutralizados, un ataque exitoso puede tener consecuencias desagradables. Por lo tanto,…
Amazon Prime Day Scams and Fake Amazon Websites
No es raro que los estafadores se dirijan a compradores en línea, a menudo haciéndose pasar por empresas como Amazon. Sin embargo, estos phishing…
Hot and Cold Crypto Wallets Hacking
Cryptocurrency is a rapidly changing world where people can make fortunes by exchanging digital assets. Sin embargo, seasoned investors and newcomers…
Google Has Disabled Some of the Global Cache Servers in Russia
Media reports say that Google is notifying ISPs in Russia…
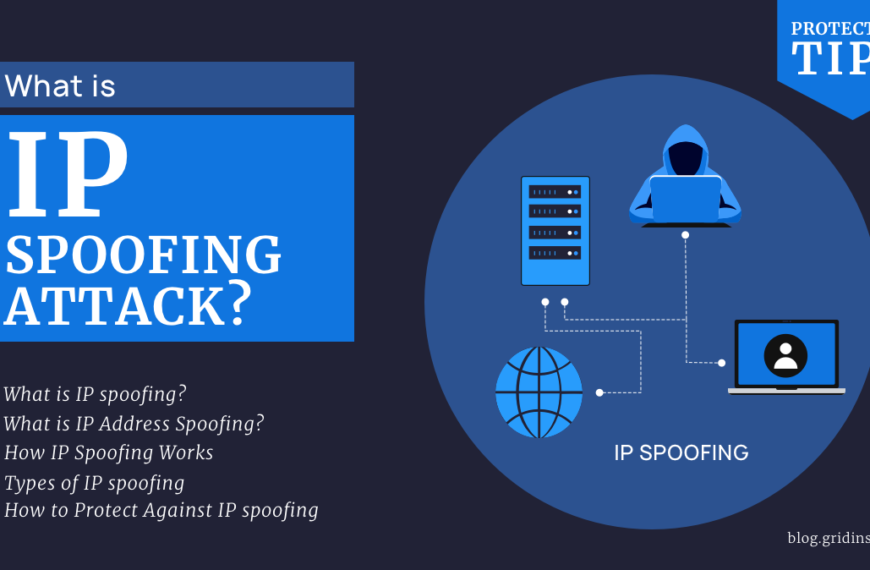
IP Spoofing Attack: Explanation & Protection
Entre otros tipos de ataque, IP spoofing stands out for…
10 Ways To Recognize and Avoid Phishing Scams
Phishing attacks are a scam that aims to steal confidential…
15 Reasons to Choose GridinSoft Anti-Malware
Choosing the anti-malware solution these days is a tough decision.…
Fake Exploits Used to Deliver Cobalt Strike Beacons
Los expertos de Cyble advierten que los ciberdelincuentes están atacando a los investigadores del EI,…
Working Tips and Recommendation: How to Use OSINT
OSINT, o inteligencia de código abierto, is a kind of reconnaissance operation…
Benefits Of Using Malware Protection
It seems that people are not aware of the benefits…
Top Threats That Anti-Malware Catches
A medida que avanza la tecnología, Los ciberataques son cada vez más frecuentes., with attackers constantly…
The Conti Ransomware Ceases Operations and Breaks Up into Several Groups
Experts report that the Conti ransomware is going out of…
10 Signs That Your Computer Is Infected With Spyware
¿Qué es el software espía?? It is a malicious program that secretly…
ARP. Address Resolution Protocol Spoofing – Detection And Prevention
ARP (protocolo de resolucion de DIRECCION) spoofing is a type of cyber…
Cybersecurity Experts Analyzed the Methods of a Group of Russian Hackers Wizard Spider
Information security specialists from PRODAFT have published the results of…