Cisco Talos has discovered a new botnet, prometei, que estuvo activo desde marzo 2020 y se centró en minar el Monero (XMR) criptomoneda. Los investigadores señalan que la botnet Prometei utiliza intensamente el protocolo SMB para su distribución.
El malware ataca principalmente a usuarios de EE. UU., Brasil, Pakistán, Porcelana, México y Chile. Durante cuatro meses de actividad, the botnet operators «ganado» acerca de $5,000, eso es, an average of about $1,250 por mes.
Do you know who else is focused on mining Monero and manipulates a variety of exploits? Lucifer! (don’t be alarmed – esto es such malware)
“The malware uses several techniques for distribution, including LOLbins (living off the land) to use legitimate Windows processes to execute malicious code (including PsExec and WMI), SMB exploits (including EternalBlue), and stolen credentials», – write Cisco Talos experts.
En total, the researchers counted more than 15 ingredients in Prometei. All of them are controlled by the main module, which encrypts (RC4) the data before sending it to the management server via HTTP.
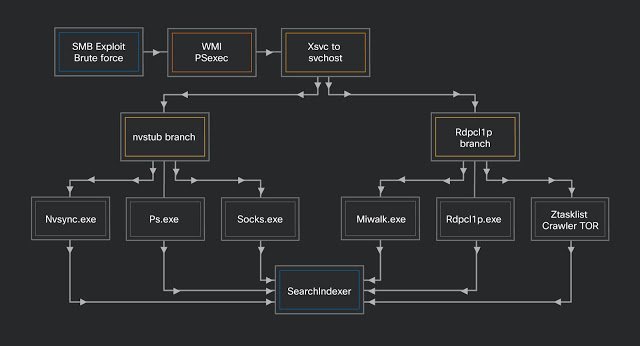
Auxiliary modules can be used to establish communication over Tor or I2P, collect system information, check open ports, spread via SMB, and scan the infected system for any cryptocurrency wallets.
Por ejemplo, a botnet steals passwords using a modified version of Mimikatz (miwalk.exe), and then passwords are passed to the spreader module (rdpclip.exe) for analysis and authentication via SMB. If that doesn’t work, the EternalBlue exploit is used for propagation.
The final payload delivered to the compromised system is SearchIndexer.exe, which is simply an XMRig versión 5.5.3.
Sin embargo, experts write that Prometei is not just a miner, the malware can also be used as a full-fledged Trojan and info-stealer.
“The botnet is split into two main branches: la C ++ branch is dedicated to cryptocurrency mining operations, and the .NET-based branch focuses on credential theft, SMB attacks and obfuscation. Al mismo tiempo, the main branch can work independently from the second one, since it can independently communicate with the control server, steal credentials and engage in mining”, – dicen los investigadores.
Cisco Talos experts point out that Prometei is unlike most mining botnets. Its authors not only divided their tools according to their purpose, it also «taught» malware to avoid detection and analysis. En particular, even in earlier versions, you can find several layers of obfuscation, which have become much more difficult in later versions.

