ESET analysts descubierto the infrastructure of a previously unknown Ramsay malware with some very interesting features. Ramsay attacks and collects data from PCs, que están aislados del mundo exterior.
Having penetrated into such a system, the malware collects Word files and other confidential documents, hides them in a special concealed container and waits for the opportunity to transfer data outside.
“We discovered the first copy of Ramsay on VirusTotal. This sample was downloaded from Japan, and it led us to discovery of additional components and versions of the platform”, – dicen los expertos.
malware, designed to steal information from machines, which are physically isolated from any networks and potentially dangerous peripherals, is very rare. Such computers are mainly used in government systems and corporate networks, y, como una regla, on them stored secret documents, as well as other secret and confidential information, incluido, por ejemplo, propiedad intelectual.
ESET researchers write that they managed to find three different versions of Ramsay, one of which was compiled in September 2019 (ramsay 1), and the other two at the beginning and end of March 2020 (Ramsay 2.a and 2.b). Ramsay infiltrates the system through malicious documents that are distributed via phishing emails or via a USB drive. Próximo, malware uses the old RCE problem in Microsoft Office to “deploy” to the system.
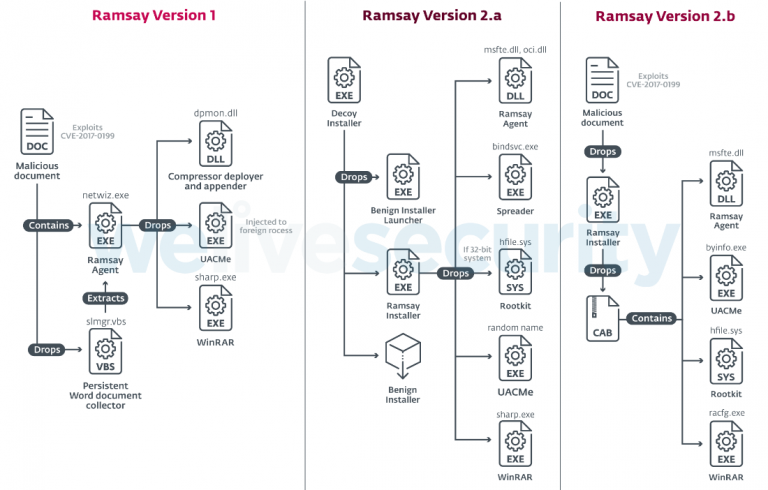
All versions of the malware are different from each other and infect victims in different ways, but the essence remains unchanged: having penetrated the system, the malware needs to scan the infected computer, collects Word, PDF and ZIP files in a hidden folder and prepares them for subsequent transfer.
Some versions have a special distribution module that adds copies of Ramsay to all PE files found on removable drives and among network resources.
“Malware could use this mechanism for distribution to reach isolated machines and networks. Después de todo, users can move infected executable files between different levels of the corporate network, and ultimately the malware will end up in isolated systems”, — dicen los investigadores.
ESET analysts admit that they were unable to determine how Ramsay retrieves data, collected on isolated machines. También, experts did not draw specific conclusions regarding the attribution of Ramsay, sin embargo, it is noted that the malware is similar to the Retro malware, which was developed by the South Korean hackers’ group DarkHotel.
Let me remind you that I recently wrote about another unusual attack, also applicable off-line – through the so-called BadUSB.