El especialista israelí en ciberseguridad Zohar Shachar hablado de su descubrimiento de la vulnerabilidad XSS en Google Maps en 2019, y luego descubrí que Google no pudo solucionarlo la primera vez.
El problema estaba relacionado con la función Google Maps que permite a los usuarios crear sus propios mapas.. Estos mapas se pueden exportar en una variedad de formatos., incluido el lenguaje de marcado de cerradura (KML), que está basado en XML y se usa comúnmente para mostrar datos geográficos en Google Earth, etcétera.
Mientras examina la respuesta del servidor al exportar un mapa usando KML, el investigador descubrió un XML que contenía, entre otras cosas, una etiqueta CDATA abierta. Shahar intentó cerrar la etiqueta con caracteres especiales y descubrió que agregar «]]>» al comienzo de la carga útil (al principio del nombre del mapa) ayuda a ir más allá de CDATA y agregar contenido XML arbitrario.
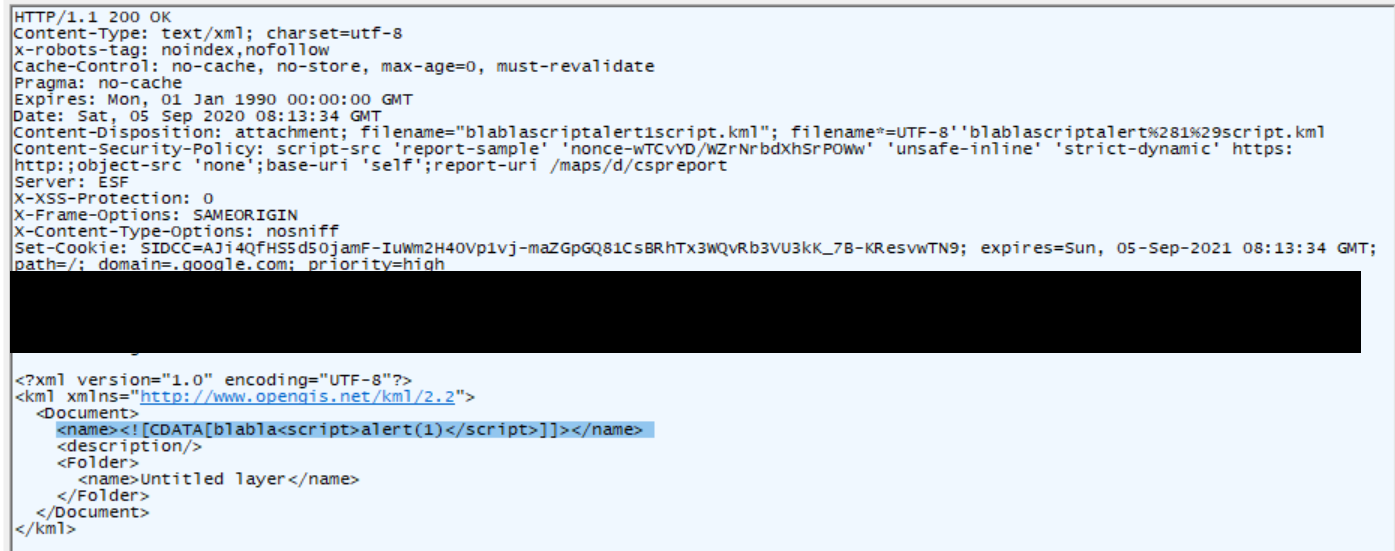
Todo esto conduce en última instancia a una vulnerabilidad XSS.. Por ejemplo, un atacante podría crear un nuevo mapa en Google Maps, equiparlo con una carga útil XSS, hacerlo público y exportarlo como un archivo KML, y luego copie el enlace de descarga.
«Después de eso, el hacker solo podía enviar el enlace a la víctima y esperar a que la víctima hiciera clic en él, inicie el exploit y ejecute el código malicioso en su navegador», - dice Zohar Shachar.
El investigador informó inmediatamente sobre el problema a Google., pero la historia no estaba terminada. Cuando Shahar recibió una notificación de que la vulnerabilidad se había solucionado y obtenido $5,000 por descubrir el error, decidió comprobar si esto era así y se sorprendió al ver que el «parche» consistió en agregar otra etiqueta CDATA.
Por lo tanto, para omitir las dos etiquetas CDATA y esta solución, El atacante solo tuvo que cerrar las etiquetas dos veces., y el exploit funcionó de nuevo.
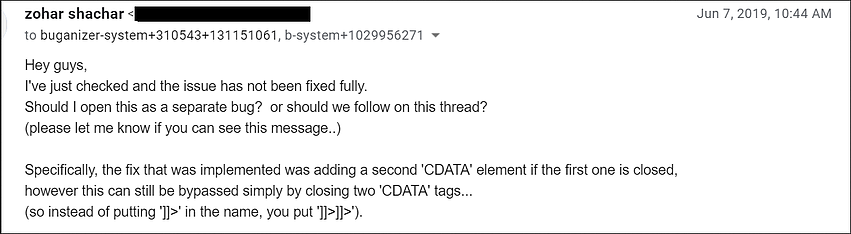
Dudar de que entendiera correctamente lo que estaba pasando. (A Shahar le parecía poco probable una solución tan simple del parche.), Sin embargo, el investigador volvió a ponerse en contacto con Google y le explicó que la solución no parecía funcionar.. Como se vio despues, Shahar tenía toda la razón. Sólo dos días después, el error fue completamente corregido, y al investigador se le pagó otro $5,000, ya que técnicamente descubrió otro problema similar.
“Después del incidente de omisión de Google Maps, Siempre reviso los parches, incluso para las cosas más simples, y vale la pena. Sinceramente les insto a todos a que hagan lo mismo”., — escribe el investigador.
Déjame recordarte que Google Maps ayuda a los usuarios a protegerse del COVID-19.

