Fin de semana pasado, uno de los proveedores de internet más grandes de Argentina, Telecomunicaciones Argentina, sufrió de REvil (Sodinokibi) ataque de ransomware. El malware ha infectado aproximadamente 18,000 ordenadores, y ahora los operadores de REvil exigen $7.5 millones de la empresa.
The ZDNet magazine escribe that the attackers managed to gain domain administrator rights, gracias a lo cual el ransomware se propagó rápidamente a 18,000 estaciones de trabajo.
“Oddly enough, this incident did not lead to problems with the Internet connection for the provider’s customers and did not affect the operation of telephony and cable TV services. Sin embargo, due to the consequences of the attack, a number of Telecom Argentina’s official websites are still not working”, – según los periodistas ZDNet.
Several employees of the affected company share on social media how the provider is coping with the crisis. It seems that immediately after the attack was detected, the company began to warn employees about what was happening, asking them to limit interaction with the corporate network, not to connect to the internal VPN network, and not to open emails with archives in attachments.
Los periodistas creen que la responsabilidad del ataque recae en el grupo de hackers REvil, basado en una publicación tuiteada que mostraba una captura de pantalla del sitio de ransomware. Basado en esta imagen, los atacantes exigieron un rescate 109,345.35 Monero (aproximadamente $7.53 millón) De la compañia. Los piratas informáticos prometieron que en caso de impago, esta cantidad se duplicaría en tres días, haciendo de esta demanda de rescate una de las más grandes de este año.
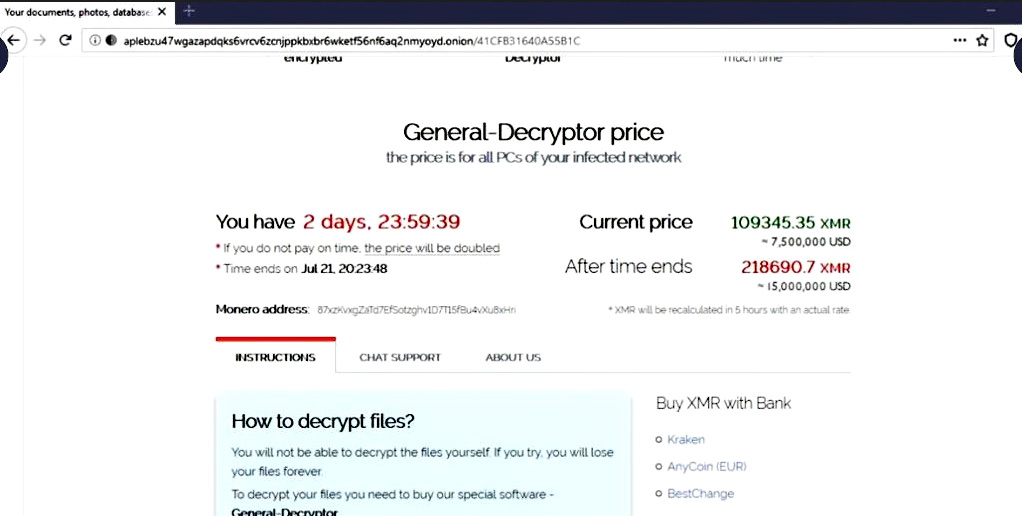
Funcionarios de Telecom Argentina aún no se han pronunciado sobre la situación., y no se sabe si la empresa tiene intención de pagar a los ciberdelincuentes.
Curiosamente, según informes de los medios locales, El ISP considera que un archivo adjunto malicioso de una carta recibida por uno de sus empleados es el punto de partida de este ataque..
“Esto no es del todo consistente con los ataques regulares de REvil., ya que el grupo suele penetrar en las empresas’ networks through unprotected network equipment. En particular, attackers are actively exploiting vulnerabilities in Pulse Secure and Citrix VPN”, – reportado en ZDNet.
Sin embargo, the specialists of the information security company Bad Packets told ZDNet journalists that Telecom Argentina not only worked with Citrix VPN servers, but among them there were systems vulnerable to the CVE-2019-19781 problema (although the patch fue lanzado many months ago).
Déjame recordarte que, information security specialists of the Danish provider KPN applied sinkholing to REvil (Sodinokibi) cryptographic servers and studied the working methods of one of the largest ransomware threats today. A very interesting analysis – I recommend it.

