Científicos de la Escuela Técnica Superior Suiza de Zurich han desarrollado un ataque que permite no introducir un código PIN al realizar pagos sin contacto con Visa Credit, Tarjetas Visa Electron y VPay. Este ataque permite a un atacante que posee los datos de una tarjeta Visa sin contacto robada utilizar la tarjeta para pagar bienes de alto valor., cuyo precio es mucho más alto que el límite de transacciones sin contacto. Y un atacante no necesita un PIN.
Un informe que describe esta técnica de ataque. ya ha sido publicado en el dominio publico, y los expertos tienen la intención de organizar una presentación completa de su investigación en el simposio del IEEE, que se celebrará en mayo 2021.
“El ataque que inventaron es muy difícil de detectar porque el atacante sería como un cliente habitual que paga una compra a través de un smartphone. En realidad, El atacante pagará con una tarjeta Visa sin contacto robada, que está escondido en algún lugar de su cuerpo”, – dicen los científicos.
Este ataque no requiere equipo sofisticado, sólo dos teléfonos inteligentes Android, una aplicación especial creada por el equipo de investigación, y la propia tarjeta sin contacto. Al mismo tiempo, La aplicación instalada en ambos smartphones funcionará como emulador de un terminal PoS y como emulador de la propia tarjeta..
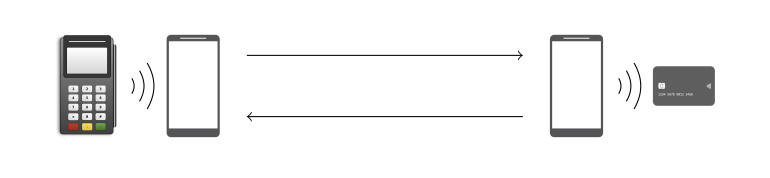
Como resultado, el ataque se ve asi: Un teléfono inteligente que imita un dispositivo PoS se coloca junto a una tarjeta robada, y un teléfono inteligente que actúa como emulador de tarjetas se utiliza para pagar bienes. La idea es que el emulador de PoS pida a la tarjeta que realice un pago y modifique los detalles de la transacción., y luego transmite los datos modificados a través de Wi-Fi al segundo teléfono inteligente, que finalmente realiza un pago grande sin tener que ingresar un código PIN (después de todo, el atacante cambió los datos de la transacción de esta manera para no requerir la entrada del PIN). A continuación se puede ver una demostración del ataque..
Nuestra aplicación no requiere rooteo ni ningún truco inteligente para Android.. Lo hemos probado con éxito en dispositivos Pixel y Huawei normales”., — escriben los investigadores.
Si hablamos del aspecto técnico del problema., Tal ataque es posible debido a fallas de diseño del estándar EMV y el protocolo sin contacto de Visa.. Estos errores permiten a un atacante modificar los datos de la transacción sin contacto, incluidos aquellos campos que son responsables de los detalles de la transacción y la necesidad de verificar el titular de la tarjeta.
Esencialmente, el atacante informa al terminal que no se requiere verificación de PIN, y que el titular de la tarjeta ya ha sido verificado en un dispositivo del consumidor (por ejemplo, un teléfono inteligente). Además, Estas modificaciones se llevan a cabo en el teléfono inteligente donde se ejecuta el emulador PoS y se realizan antes de enviarse al segundo teléfono inteligente.. Eso es, La información ya modificada se transmite al dispositivo PoS real., y no puede determinar si los detalles de la transacción han sido modificados.
Para encontrar estos problemas, los investigadores utilizaron una versión modificada de una herramienta llamada Tamarin, que se utilizaba anteriormente para detectar vulnerabilidades complejas en TLS 1.3 protocolo criptográfico (PDF), así como en el mecanismo de autenticación 5G (PDF).
Usando la misma herramienta, Los expertos identificaron otro problema potencial que afecta no solo a Visa sino también a Mastercard.. Los investigadores no realizaron pruebas de campo de este error por razones éticas..
Así describen los expertos el segundo problema:
También, Nuestro análisis simbólico reveló que durante una transacción sin contacto fuera de línea utilizando una tarjeta Visa o una Mastercard antigua, la tarjeta no está autenticada con el terminal a través de ApplicationCryptogram (C.A.) – una prueba criptográfica de la transacción creada por la tarjeta que el terminal no puede verificar (sólo el emisor de la tarjeta puede) … Esto permite a los atacantes engañar al terminal para que acepte una transacción fuera de línea no válida.. Más tarde, cuando el adquirente agrega los datos de la transacción al registro de compensación, el banco emisor encontrará el criptograma incorrecto, pero en ese momento, el criminal ha desaparecido hace mucho tiempo junto con los bienes».
Déjame recordarte que también hablé de lo interesante. Técnica SpiKey que permite abrir la cerradura grabando el sonido de una llave al girar. Además, pronto será producido un verdadero hacker Tamagotchi. ¿Sientes ya tu propia indefensión en el nuevo mundo digital??

