Como parte de la “Actualización del Martes” de junio,” Intel fixed more than 20 different vulnerabilities in its products, including the SGAxe bug, which endangers several Intel processors.
The manufacturer also released updated microcodes for processors vulnerable to the new CrossTalk MDS problem. But CrossTalk was not limited to this, and this week se hizo conocido about another problem that also threatens Intel processors. This no less serious vulnerability is called SGAxe, and it is a variation of the speculative attack CacheOut, discovered in early 2020.
Let me remind you that CacheOut belongs to the class of vulnerabilities of Microarchitectural Data Sampling (MDS), which includes ENIGMA, Fallout y carga zombie, and rna can lead to data leakage from Intel processors, virtual machines and SGX enclaves. It’s also worth noting that CacheOut is a kind of successor to another processor problem, Foreshadow, which first used the L1 cache to extract SGX keys.
“The measures Intel took to eliminate side-channel attacks on SGX (firmware updates and new architectures) were not enough”, – said representatives of the research team that discovered CacheOut and SGAxe problems.
Debido a esto, exploitation of the SGAxe problem allows an attack of the transient execution type, which leads to the restoration of trusted by the Intel certification center SGX cryptographic keys.
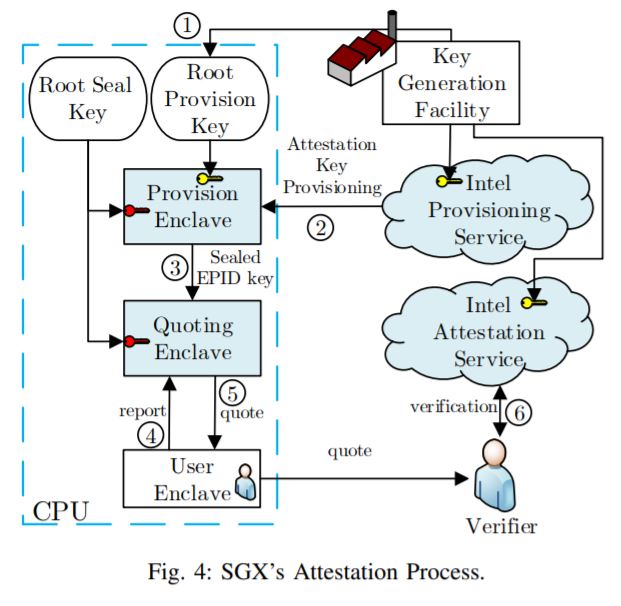
El certification mechanism is an important part of SGX. De hecho, con su ayuda, enclaves can prove to third parties that they are correctly initialized and work on a true Intel processor. En particular, this allows making sure that the software running inside the CPU has not been superseded. De este modo, extracting SGX certification keys allows attackers to pretend to be a legitimate Intel SGX machine from a cryptographic point of view.
Researchers note that the attack will work even if the SGX enclave is in standby mode, por lo tanto, it bypasses all hardware defenses.
“If the certification keys of a machine are compromised, any secrets provided by the server can be read right away by an untrusted client host application, while all output supposedly created by client-side enclaves cannot be considered reliable. De hecho, it makes all SGX-based DRM applications useless, as any secret can be easily restored”, — experts explain.
A complete list of processors for which SGAxe is dangerous has been published by Intel Product Security Incident Response Team (PSIRT) and can be seen aquí.
Although Intel have already released fixes for the CacheOut problem in January, now it is planned that Intel will update the microcode again to protect against CacheOut and SGAxe and address the root cause of these vulnerabilities.
The company will also restore the Trusted Compute Base (TCB), which will invalidate all previously signed and compiled certification keys.
“This process ensures that your system is in a safe mode and can reuse remote certification”, — escriben los investigadores.
Let me remind you that we talked about the attacks of Snoop y Inyección de valor de carga, which also possess serious threats to Intel.

