Security expert Peter Dantini descubierto that the Shlayer malware bypassed Apple’s checks: pasó con éxito el proceso de certificación notarial del software y pudo ejecutarse en cualquier Mac con macOS Catalina y versiones posteriores.
En febrero de este año, Apple introdujo un nuevo mecanismo de seguridad: any Mac software distributed outside the App Store must go through a notarization process in order to run on macOS Catalina and above.
“Basically, any software for the Mac now has to go through an automated scan at Apple for malware and code signing issues. Si se pasan los controles, the Gatekeeper allows the application to run on the system”, – explained Apple experts.
En Twitter, Peter Dantini writes that Apple’s automated checks do not seem to be very reliable. The researcher discovered that Shlayer malware installers were distributed through the malicious site Homebrew, which had passed the notarization (as usual, under the mask of updates for the Adobe Flash Player). Por lo tanto, they could be run even on the latest macOS 11.0 Big Sur.
Dantini’s find was confirmed by another well-known expert, Patricio Wardle, OMS writes in a blog that he immediately notified Apple of the notarized malware, and the company revoked Shlayer’s certificates on the same day, Agosto 28, 2020. This means that the Gatekeeper will now automatically block them.
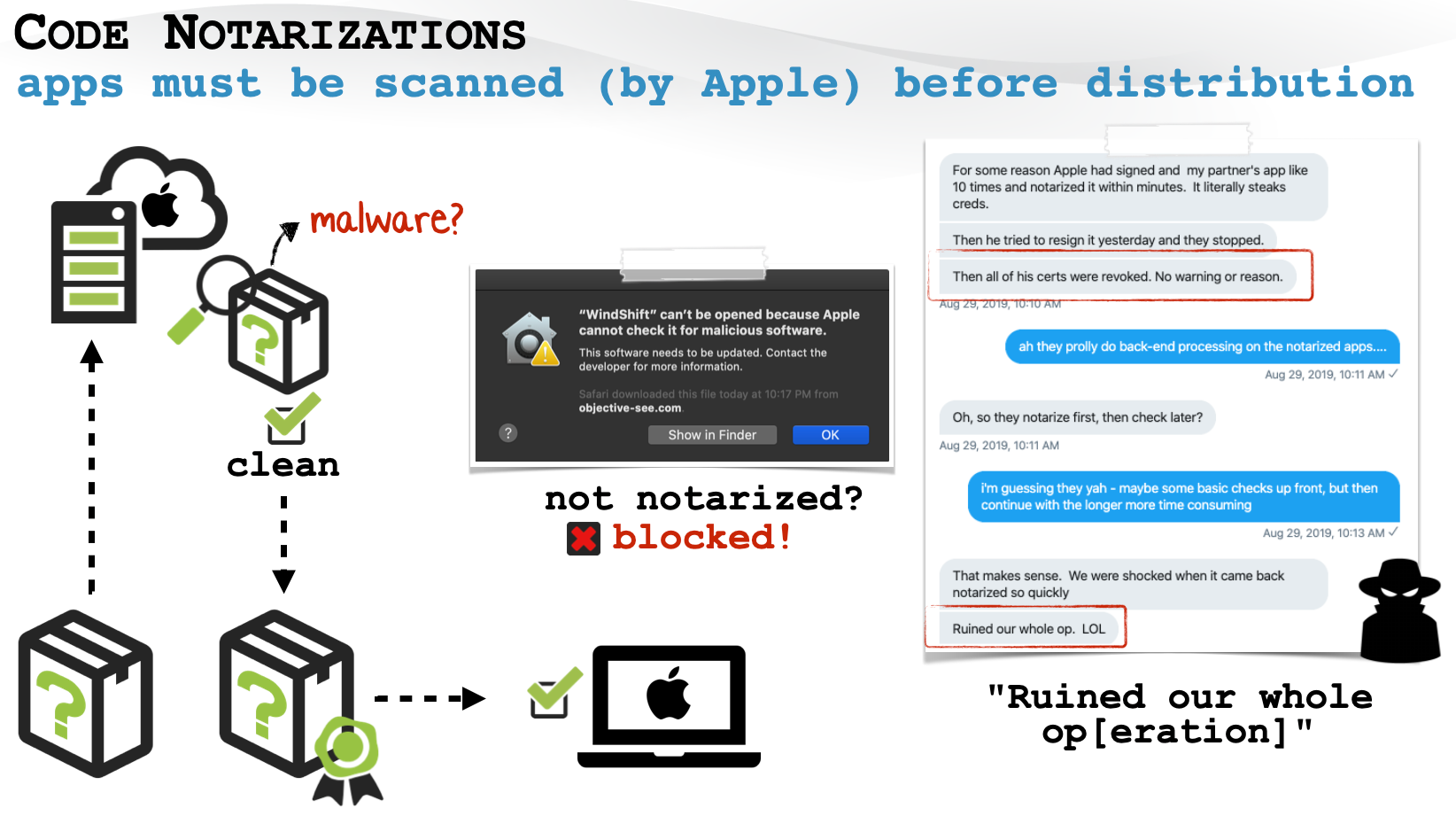
Sin embargo, over the last August weekend, a researcher found that the Shlayer campaign was still picking up steam, with offering users new notarized payloads the same day Apple revoked the original certificates. World writes that the old and new payloads are almost identical – they contain OSX.Shlayer, also Bundlore adware.
“It is obvious that in the endless game of cat and mouse between malefactors and Apple, malefactors are still winning”, — concludes the expert.
According to Kaspersky Lab, Shlayer has been the most widespread threat for macOS for two years now: en 2019, every tenth user of the company’s security solutions encountered this malware at least once, and its share in relation to all detections on this OS is almost 30%.
The first copies of the Shlayer family fell into the hands of researchers back in February 2018. Al comienzo de 2020, casi 32,000 different malicious Trojan samples were collected, and were identified 143 C&C domains.
Más amenudo, Los troyanos de la familia Shlayer descargan e instalan diversas aplicaciones de publicidad en el dispositivo del usuario. Además, su funcionalidad teóricamente permite descargar programas que no sólo inundan a los usuarios con anuncios, sino también abrir espontáneamente páginas publicitarias en los navegadores y reemplazar los resultados de búsqueda para descargar aún más mensajes publicitarios.
Let me also remind you that recently Google experts talked about vulnerabilities in Apple sistemas operativos.

