Consejos & Trucos
PUA:Win32/Presenoker
PUA:Win32/Presenoker es un adware diseñado para ganar dinero mostrando anuncios intrusivos y recopilando datos. Este malware puede tomar el control…
USB Shortcut Virus
Virus de acceso directo USB, es un programa malicioso que altera los archivos de los discos. It is a rather old…
Personal Data vs. Sensitive Data: What is the Difference?
La tecnología es cada vez más importante en nuestros hogares, negocios, y dispositivos personales. Como resultado, we are generating more personal data…
Data Breach & Data Leaks
Las fugas de datos y las violaciones de datos son fenómenos muy similares con una ligera diferencia en el principio de acción.. It was…
Virus:Win32/Grenam.VA!MSR
Virus:Win32/Grenam.VA!MSR es un tipo de malware que puede ingresar sigilosamente al sistema y establecer conexiones remotas.. Permite a los atacantes…
Malware Propagation On Darknet Forums
The forums on the dark web are well-known for being…
Credentials Theft is On The Rise
Email spam has become the prevalent form of phishing and…
How to Protect Your Digital Footprint
The modern business world has been greatly advanced by the…
RDP Honeypot Was Attacked 3.5 Million Times
Con mayor trabajo remoto, IT teams use remote access tools…
Third Party Data Breach: Definition and How to Prevent It
En el panorama digital actual, data breaches have become an alarming…
Beware of Vacation-Related Scams: 4 Most Prevalent Types
Email scam actors constantly try to pick a better disguise…
BlackCat Ransomware New Update Boosts Exfiltration Speed
BlackCat ransomware continues to make a fuss globally for the…
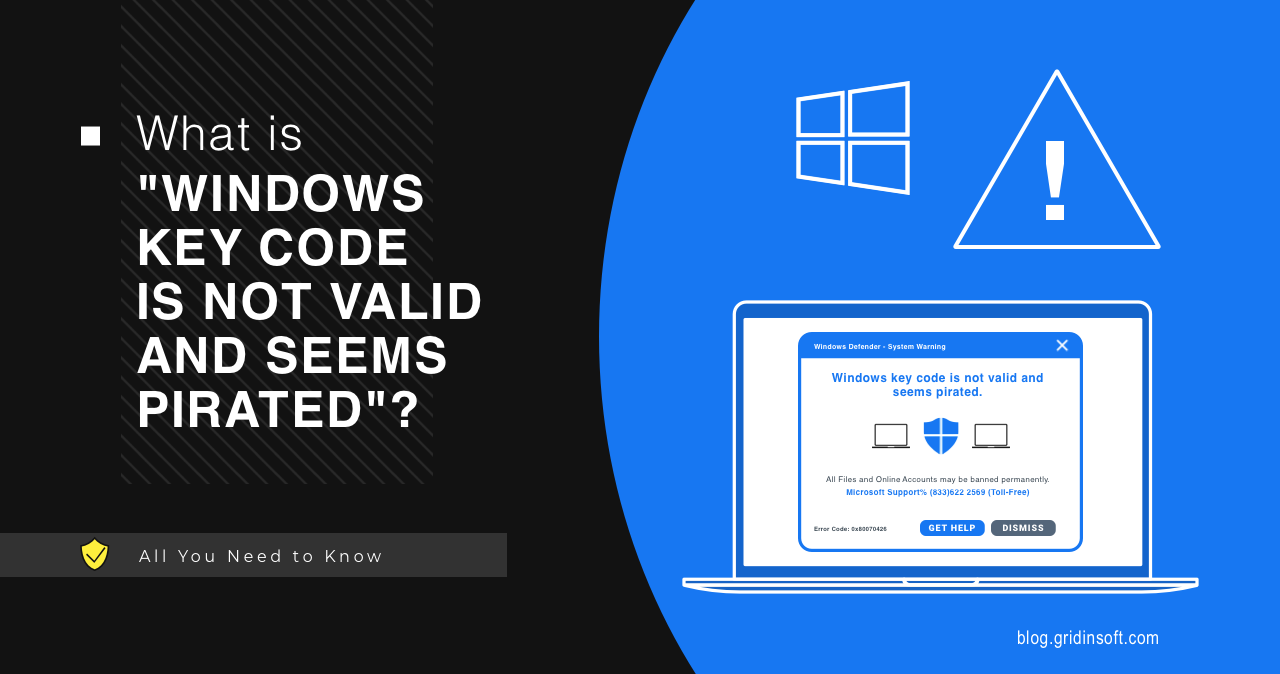
What is «Windows Key Code Is Not Valid And Seems Pirated»?
Windows Key Code Is Not Valid And Seems Pirated appears…
How to Defeat Insider Threat?
En el mundo digital actual, organizations face more risks than…
Conti Ransomware Heritage in 2023 – What is Left?
Los grupos de ransomware van y vienen, but the people behind them…
What is Business Email Compromise (BEC) Attack?
Ataque de compromiso de correo electrónico empresarial, o en breve BEC, is a relatively…
DDoS-For-Hire Services Used by Hacktivists in 2023
Most people think you must be a hacker to participate…