Consejos & Trucos
Taskbarify Unwanted Application
Taskbarify es un software no deseado que afirma ser un pequeño modificador de Windows. Sin embargo, it also turns the device into…
Trojan:Win32/Vigorf.A
Trojan:Win32/Vigorf.A es una detección genérica de Microsoft Defender. This detection commonly identifies a running loader malware that may deal significant…
Trojan:Win32/Znyonm
Trojan:Win32/Znyonm es una detección que se ve a menudo durante la actividad de malware de puerta trasera en segundo plano.. Este tipo de malware puede aumentar los privilegios, enable…
Win32/Wacapew.C!ml Detection Analysis & Recommendations
Win32/Wacapew.C!ml detection refers to programs that have suspicious properties. This can be either a false positive or a detection of…
PUABundler:Win32/uTorrent_BundleInstaller
PUABundler:Win32/uTorrent_BundleInstaller es una detección de Microsoft Defender asociada con el instalador del otrora popular cliente uTorrent.. Es…
Safari Can’t Establish a Secure Connection Error
El «Safari no puede establecer una conexión segura» error message appears…
Spyware vs. Stalkerware: What’s the difference?
Los estafadores desarrollan diversos métodos para penetrar la propiedad ajena,…
What is Torrenting? Is it illegal or Safe? How Does it Work
A torrent is a tool for free data exchange on…
«Get Rich With Bitcoin» Instagram Bitcoin Scams
Instagram is a vast social network with over a billion…
How to Access the Dark Web Safely: Useful Tips for the Darknet
¿Es legal la web oscura?? Despite Darknet’s association with illegal…
Why Phishing is Still the Most Common Cyber Attack?
Desgraciadamente, millions of users worldwide are at risk every single…
Common Cryptocurrency Scams and Frauds: How to Avoid
Fraudsters do not stand still and are always looking for…
TikTok Scams Stealing Money And Data. Beware!
TikTok has become a popular social network with over a…
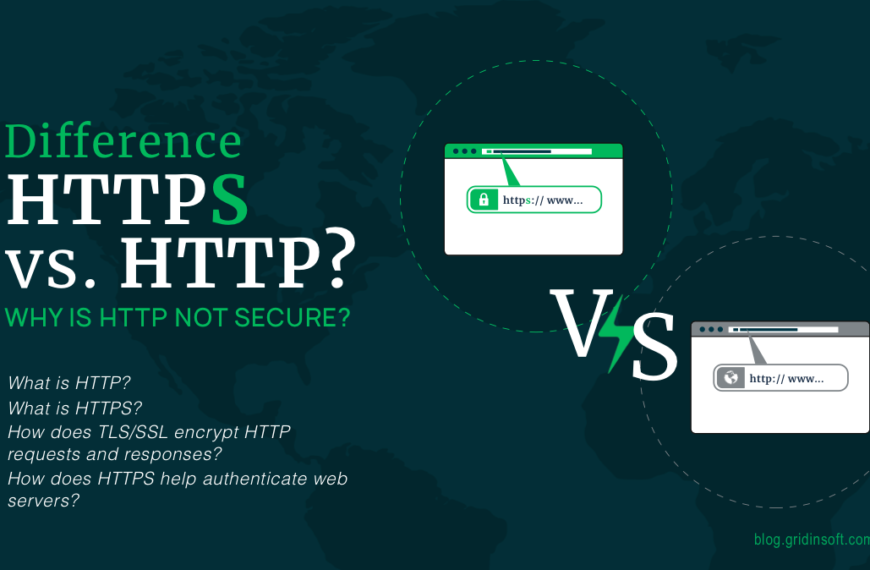
Difference HTTPS vs. HTTP? Why is HTTP not secure?
Cualquier página web se almacena en un servidor., a computer…
Trackid=sp-006 — What is this thing?
Cookie tracking is a kind of network activity on the…
Signs of Identity Theft: How to Prevent It?
El robo de identidad es un delito bastante desagradable. Cybercriminals can not…
Pegasus Spyware — The Most Dangerous Malware
Pegasus Spyware is a malicious program that is covered with…











![Signs of Identity Theft: How to Prevent Identity Theft [Short Guide 2022 ]](https://es.gridinsoft.com/blogs/wp-content/uploads/2022/09/istockphoto-1279316333-612x612-1.jpg)
