Apple pagó $75,000 to the IS researcher Ryan Pickren in the frameworks of the bug bounty program for vulnerabilities in Safari, due to which it was possible to access someone else’s cameras on Mac, iPhone y iPad, simply by directing a person to a special site.
En total, Picren discovered seven vulnerabilities in the Apple browser and the Webkit browser engine (CVE-2020-3852, CVE-2020-3864, CVE-2020-3865, CVE-2020-3885, CVE-2020-3887, CVE-2020-9784 , CVE-2020-9787), three of which can be linked together and used to track users through the camera and microphone on an iPhone, iPad or Mac.
For such an attack, just a little is required: for the victim to enter a malicious site. No other interaction is required, and a malicious site can pretend to be a popular legitimate resource and abuse the permissions that the victim would grant only to a trusted domain.
“If a malicious site needs to access the camera, all that it needs to mask itself as a reliable site for video conferencing, such as Skype or Zoom”, — the researcher notes.
Corrections for bugs found by the specialist were released as part of Safari 13.0.5 (release dated January 28, 2020) y Safari 13.1 (release dated March 24, 2020).
Picren explains that Safari creates access to devices that require specific permissions (such as camera, microphone, ubicación, etcétera) for each individual site. This allows individual sites, such as the official Skype site, to access the camera without asking for user permission with each start.
En iOS, there are exceptions to this rule: if third-party applications must require user’s consent to access the camera, then Safari can access the camera or photo gallery without any permissions.
Exploitation of the problems became possible due to the way the browser parses URL schemes and processes the security settings for each site. En este caso, the researcher’s method works only with sites already open in the browser.
“The most important fact is that the URL scheme is completely ignored,” the expert writes. – This is a problem, as some schemes do not contain a meaningful host name at all, for example file:, javascript: o datos:. Simply, the error makes Safari think that the malicious site is actually trusted one. This is due to exploitation of a number of shortcomings (how the browser parses the URI, manages the web origin and initializes the secure context).»
De hecho, Safari cannot verify that the sites adhered to Same Origin policies, thereby granting access to another site that should not have been granted permission at all. Como resultado, the site https://example.com and its malicious counterpart fake://example.com may have the same permissions. Por lo tanto, you can use file: URI (por ejemplo, archivo:///path/to/file/index.html) to trick the browser and change the domain using JavaScript.
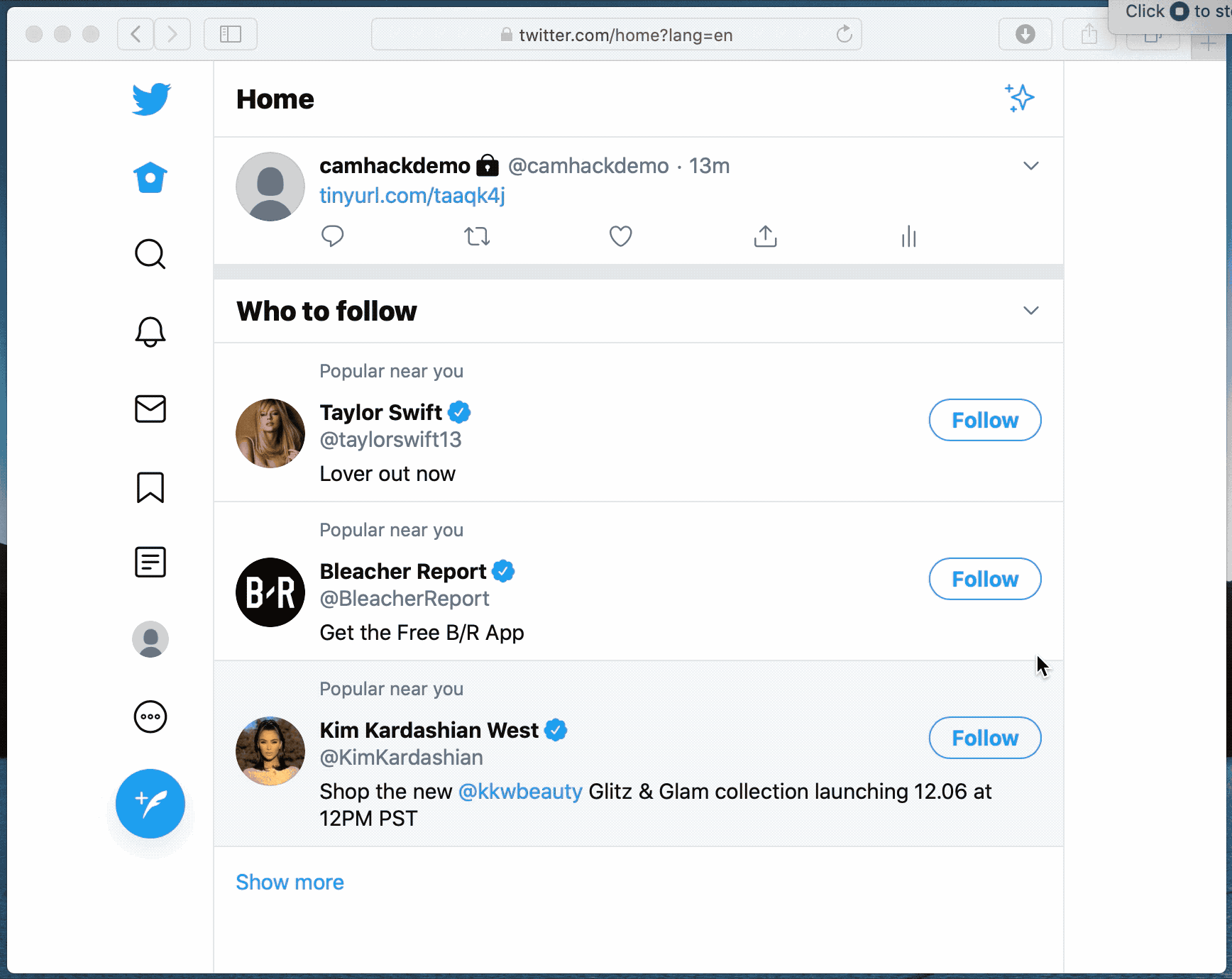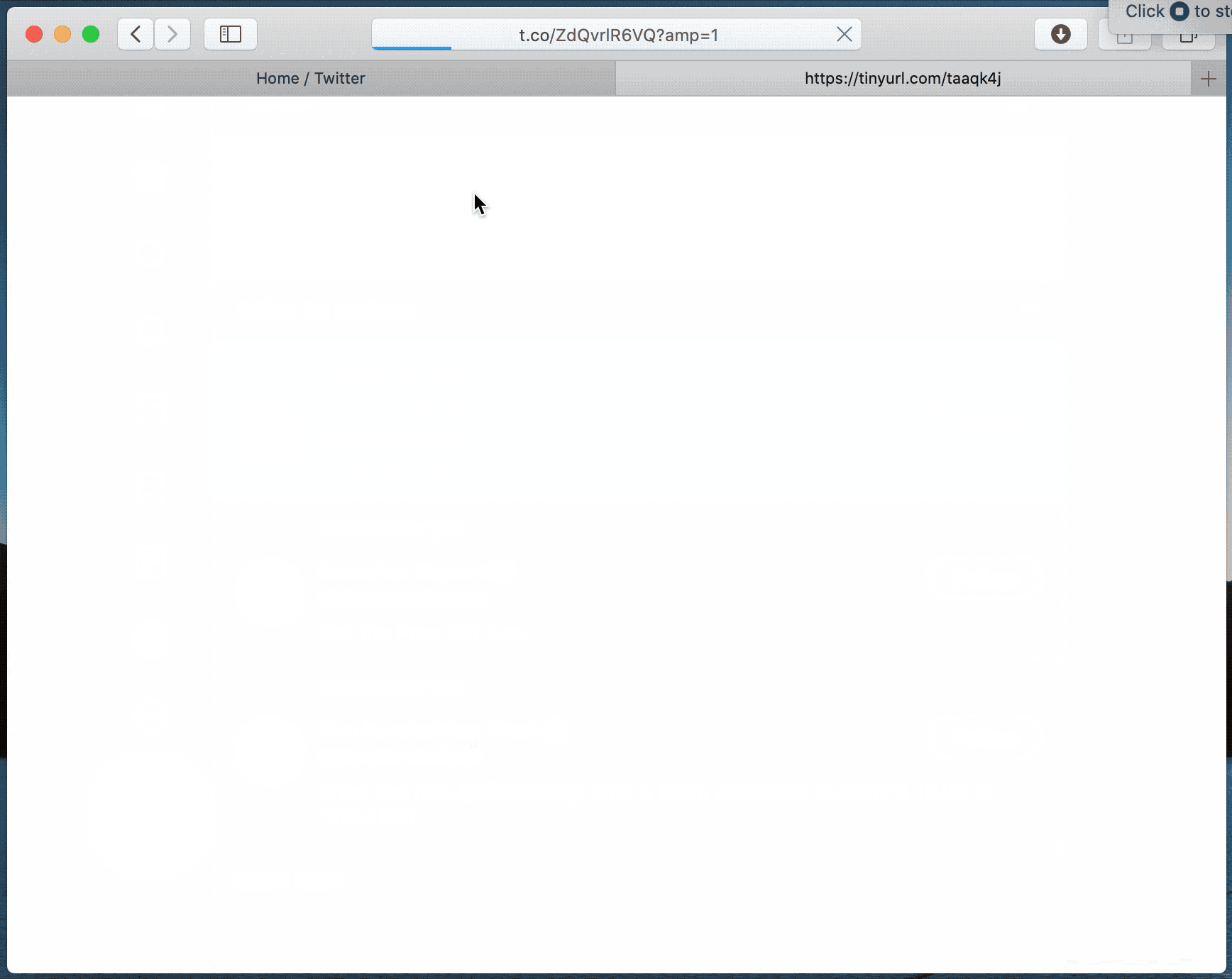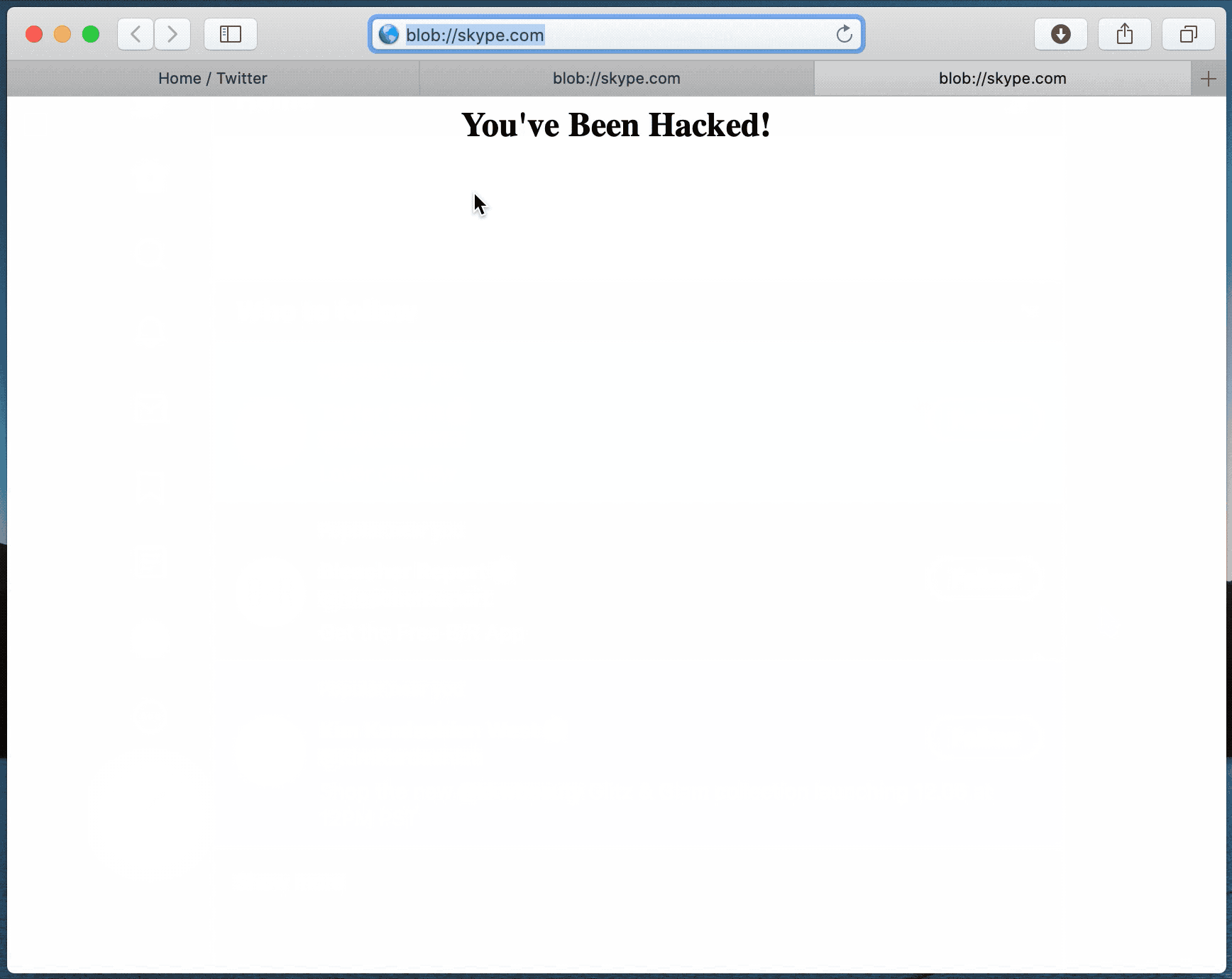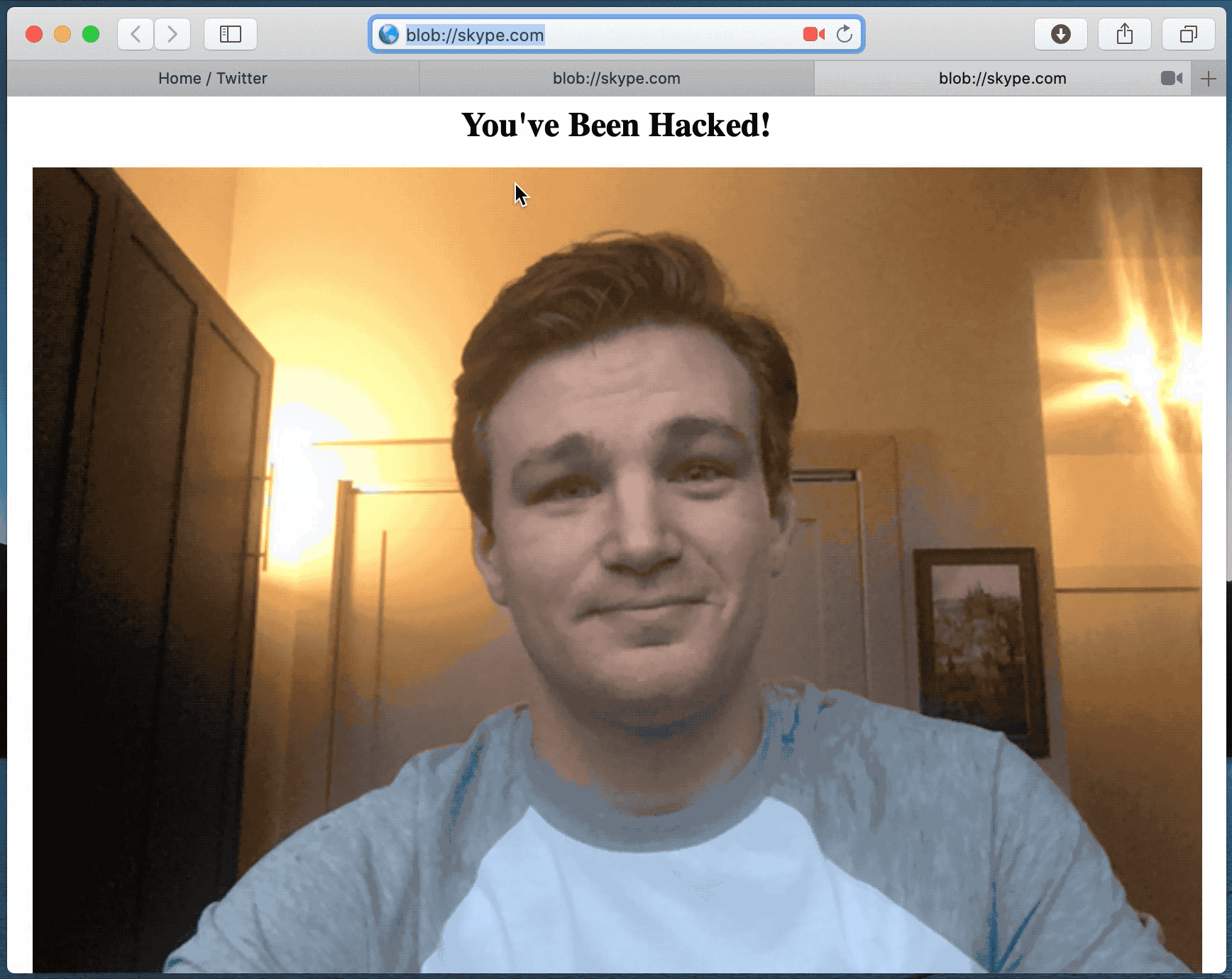
“Safari believes we are on skype.com and I can download some kind of malicious JavaScript. Camera, Screen Sharing microphone will be compromised after opening my local HTML file”, — Ryan Pickren writes.
Similarly works the blob URL: (por ejemplo, blob://skype.com) can be used to run arbitrary JavaScript code, using it to directly access the victim’s webcam without permission.
Peor aún, the study showed that unencrypted passwords can be stolen in the same way, since Safari uses the same approach to detect sites that require automatic password completion.
PoC exploits and a demonstration of the attacks described are available on the specialist Blog.
I should also remind you that recently researcher remotely hacked iPhone usando solo una vulnerabilidad.

