Los expertos advirtieron que las vulnerabilidades en el antiguo GTP (GPRS Tunneling Protocol) could quite seriously affect the operation of 4G and 5G networks.
In reports published last week and en diciembre 2019, Positive Technologies and A10 Networks described in detail a number of vulnerabilities in this protocol. En particular, are known the following problems:
- Disclosure of subscriber information (including location data that can be used to track users);
- suplantación de identidad, which can be used by scammers, as well as for attacks that allow posing as another user;
- negación de servicio (Del) attacks on network equipment, resulting in massive disruption to mobile communications.
Researchers explain that mobile providers will be forced to support GTP in their 5G networks, y a causa de esto, users will remain vulnerable, although 5G contains improvements to prevent such attacks.
GTP is a mechanism for connecting different networks by creating IP tunnels between different devices and the mobile network. Inicialmente, the protocol was developed as a method of connecting different providers of GPRS communications (2.5GRAMO) and allowed users to navigate the networks of different operators, but at the same time retain access to such functions as SMS, MMS, WAP and so on. Sin embargo, with the development of new protocols (3G and 4G), GTP began to act as a bridge between old and new technologies.
"Desafortunadamente, in the days when GTP was developed, security was not a priority and it was not laid during the design. De hecho, GTP does not even support such a basic thing as sender authentication and does not verify the actual location of the user”, – say Positive Technologies experts.
This means that anyone can send a GTP packet with fake data to the infrastructure of the mobile operator, and the latter will accept it as legitimate traffic, not having the opportunity to check whether the packet was received from one of the real subscribers. Because of this feature of GTP, researchers have more than once discovered various possibilities of abuse of GTP with the aim of attacks against 2.5G-, 3G-, 4G-, and now 5G-networks.
en su informe, Positive Technologies experts say that in 2018-2109 they conducted a security audit of 28 mobile operators in Europe, Asia, África y Sudamérica. The study examined both 4G networks and 5G networks.
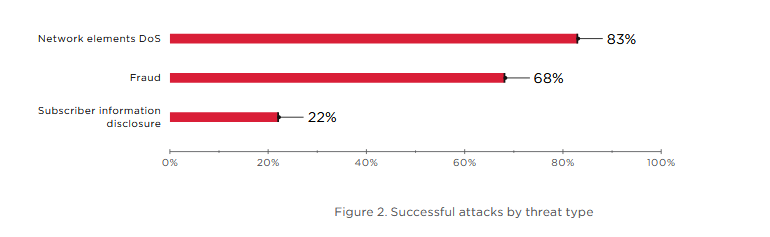
Majority of studied by analysts networks (both 4G and 5G) were vulnerable to old attacks through GTP. The protocol is currently used on 4G-5G mixed networks, but the protocol will also be supported on 5G networks that are just starting to deploy.
Experts emphasize that GTP security problems will not disappear even after switching to 5G, por lo tanto, 5G network operators need to protect their legacy GTP integrations by deploying additional systems for authentication and authorization of subscribers. The company also encourages operators to perform IP filtering based on the white list at the GTP level, and follow GSMA recommendations for real-time traffic analysis and timely measures to prevent fraudulent activity.
“The GTP protocol contains a number of vulnerabilities that threaten both mobile operators and their customers. Como resultado, attackers can interfere with the operation of network equipment and leave the whole city unconnected, impersonate other users, and also use network services at the expense of the operator or its subscribers, — states the Positive Technologies report. — Massive loss of communication is especially dangerous for 5G networks, as their subscribers are IoT devices, equipo industrial, smart homes and urban infrastructure.”
A propósito, do you know that La vulnerabilidad IMP4GT en LTE amenaza a casi todos los teléfonos inteligentes modernos?

